| CPC H04L 63/0428 (2013.01) [G06F 16/951 (2019.01); G06N 7/01 (2023.01); H04L 9/14 (2013.01); H04L 9/3236 (2013.01); H04L 9/3297 (2013.01); H04L 63/061 (2013.01); H04L 63/12 (2013.01); H04L 63/1408 (2013.01); H04L 63/1433 (2013.01); G06N 5/01 (2023.01); G06N 5/045 (2013.01); G06N 5/046 (2013.01); G06N 20/00 (2019.01); H04L 9/50 (2022.05); H04L 63/0442 (2013.01); H04L 63/123 (2013.01)] | 7 Claims |
|
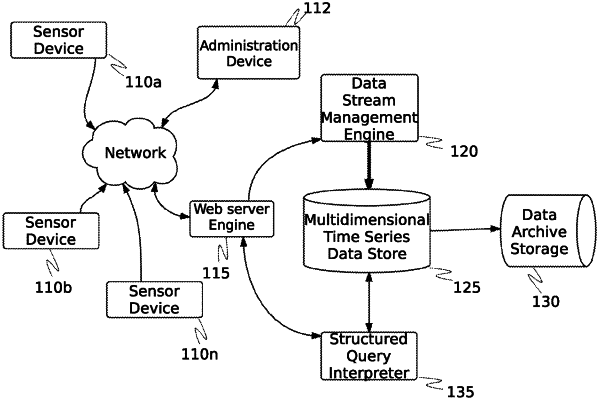
1. A system for fingerprint-based network mapping of cyber-physical assets, comprising:
a first computing device coupled to a physical asset and comprising a first processor, a first memory, a geolocation device, and a first plurality of programming instructions that, when operating on the first processor, cause the first computing device to:
periodically determine a geographical location of the physical asset using the geolocation device;
generate an encrypted asset status update message, the status update message comprising a device identifier of the first computing device and the geographical location of the physical asset; and
transmit the encrypted asset status update message via a network to a second computing device; and
a port scanner comprising at least a second processor, a second memory, and a second plurality of programming instructions that, wherein the second programmable instructions, when operating on the second processor, cause the port scanner to:
receive the encrypted asset status update message from the first computing device;
retrieve a plurality of stored fingerprint records from the second memory or a database, at least one of the plurality of fingerprint records corresponding to the first computing device;
perform a scan of one or more ports of the first computing device, the scan being based on the corresponding fingerprint record;
analyze the results of the scan;
if the analysis indicates that the results do not match the corresponding fingerprint record, transmit an encrypted failure notification to the second computing device; and
if the analysis indicates that the results match the corresponding fingerprint record, transmit an encrypted success notification to the second computing device;
wherein the second computing device verifies the authenticity of the received encrypted success and failure notifications and, for each verified encrypted success notification, modifies a cyber-physical graph based upon the encrypted asset status update message.
|