| CPC H04L 63/029 (2013.01) [H04L 63/0236 (2013.01); H04L 63/0272 (2013.01); H04L 63/0435 (2013.01); H04L 63/061 (2013.01)] | 14 Claims |
|
1. A method comprising:
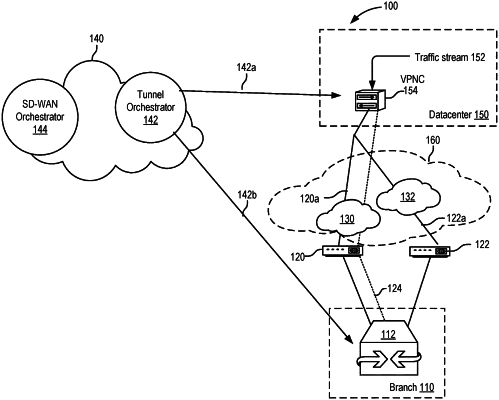
detecting, at a first network device between a second network device and a third network device, an Internet Key Exchange protocol (IKE) key negotiation between the second network device and the third network device;
based on detecting the IKE key negotiation between the second network device and the third network device, creating a firewall session in the first network device between the second and third network devices, wherein a first Internet Protocol Security (IPSec) tunnel is established through the first network device between the second and third network devices using the IKE key negotiation, the first tunnel being compliant with the firewall session and allowing passage of IPSec data packets through the first network device between the second and third network devices;
passing, through the first network device based on the establishment of the first tunnel, the IPSec data packets exchanged between the second and third network devices using cloud-managed IPSec keys from a cloud-based orchestrator, wherein the IPSec data packets are exchanged as part of a hand-shake operation that results in an establishment of a second tunnel between the second and third network devices according to the cloud-managed IPSec keys, wherein the second tunnel is an overlay tunnel on an underlay network; and
after the establishment of the second tunnel and the cloud-managed IPSec keys are active, discarding the negotiated IKE and taking down the first IPSec tunnel gracefully without disrupting encrypted communications between the second and third network devices.
|