| CPC H04L 63/0209 (2013.01) [G06N 20/00 (2019.01); H04L 63/0236 (2013.01); H04L 63/1433 (2013.01); H04L 63/20 (2013.01)] | 15 Claims |
|
1. A method comprising:
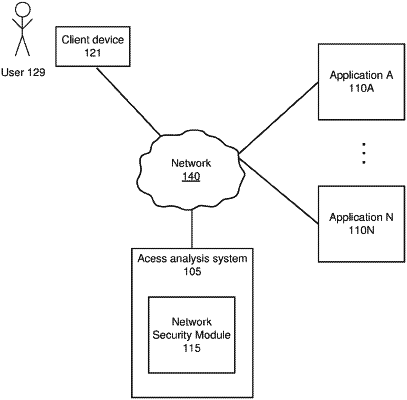
receiving connection data corresponding to network requests of client devices associated with a network, wherein an item of the connection data includes at least one network address;
training a machine learning model using the connection data, wherein the machine learning model is configured to output scores for network zones input into the machine learning model;
receiving a network zone;
inputting the network zone into the machine learning model to obtain a corresponding score, the corresponding score representing a security of the network zone relative to the network;
displaying data to a network administrator, the data representing the corresponding score and a recommendation;
receiving an approval of the recommendation from the network administrator; and
modifying a network operation of the network based on the corresponding score after receiving the approval.
|