| CPC G06Q 40/03 (2023.01) [G06Q 20/20 (2013.01); H04L 9/0861 (2013.01); H04L 9/14 (2013.01); H04L 9/30 (2013.01); H04L 9/3226 (2013.01); G06Q 20/4014 (2013.01); G06Q 30/0226 (2013.01); G06Q 2220/00 (2013.01); H04L 2209/56 (2013.01)] | 9 Claims |
|
1. A point of sale computing device configured for facilitating a loan allocation transaction including an automobile financing transaction over at least two transaction phases, the loan allocation transaction based on a multi-layer cryptographically secure data structure, the point of sale computing device including:
at least one processor configured to:
maintain a corresponding vendor second key in a secure data storage, the vendor second key corresponding to a vendor first key;
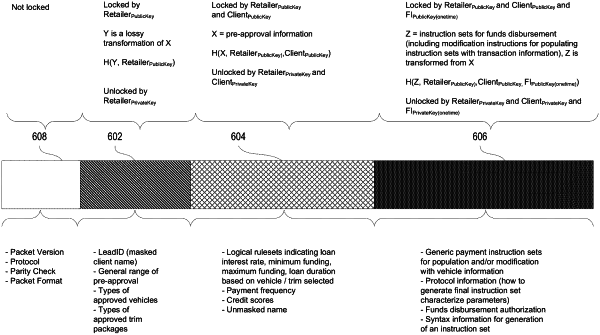
receive, and store in the secure data storage, the multi-layer cryptographically secure data structure having at least two portions including:
a first portion encapsulating a first data payload representative of unmasked pre-approval data and masked pre-approval data, the first data payload encrypted using at least with the vendor first key; and
a second portion encapsulating a second data payload including inverse transformation data for un-obfuscating the masked pre-approval data, the second data payload encrypted at least with a first combination of a client first key and the vendor first key, the client first key being reversible with a corresponding client second key;
decrypt, during a first transaction phase, the first portion based on the corresponding vendor second key to access the unmasked pre-approval data, wherein the masked pre-approval data represents obfuscated data in the absence of a decrypted second portion;
communicate during the first transaction phase the unmasked pre-approval data of the first portion at a user interface;
decrypt, during a second transaction phase, the second portion using a combination of the client second key and the vendor second key to access the inverse transformation data;
unmasking the masked pre-approval data upon decrypting the second portion by combining the inverse transformation data and the masked pre-approval data; and
communicate a set of loan allocation transaction options based on unencrypted and unmasked pre-approval data accessible upon decrypting the first portion and the second portion during the respective first transaction phase and the second transaction phase,
wherein the data structure is a tripartite data structure including the first portion, the second portion, and a third portion;
wherein the at least one processor includes a dedicated secure crypto-processor configured to decrypt the data structure independently of the corresponding computing devices associated with the client, the point of sale, and the financial institution such that none of the corresponding computing devices associated with the client, the point of sale, and the financial institution are able to access the data structure during decryption, and the secure data storage interconnects only with the dedicated secure crypto-processor; and
wherein the dedicated secure crypto-processor is housed in a secure enclave in a computer motherboard.
|