| CPC G06Q 20/4016 (2013.01) [G06N 20/00 (2019.01); G06Q 40/12 (2013.12)] | 21 Claims |
|
1. A fraudulent financial transaction detection method performed by a computer apparatus comprising processing circuitry, the fraudulent financial transaction detection method comprising:
collecting, by the processing circuitry, transaction details from a financial institution;
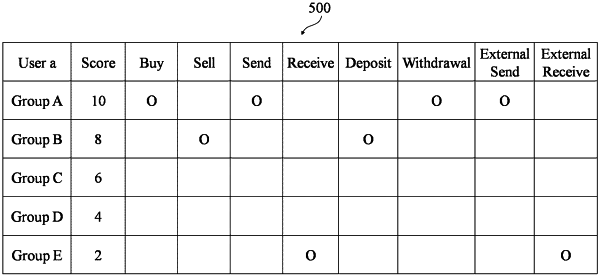
first classifying, by the processing circuitry, each of a plurality of users into one among a set of first risk groups for a first transaction action type, the plurality of users corresponding to the transaction details, and each respective user among the plurality of users being classified into a corresponding first risk group among the set of first risk groups;
second classifying, by the processing circuitry, each of the plurality of users into one among a set of second risk groups for a second transaction action type, each respective user among the plurality of users being classified into a corresponding second risk group among the set of second risk groups, the second transaction action type being different from the first transaction action type;
determining, by the processing circuitry, whether a first user among the plurality of users is in a high-risk group based on a sum of scores set for a first set of risk groups, the first set of risk groups including,
the corresponding first risk group into which the first user is classified, and
the corresponding second risk group into which the first user is classified; and
blocking, by the processing circuitry, a requested transaction in response to determining the first user is in the high-risk group.
|