| CPC G06F 9/45558 (2013.01) [G06F 9/455 (2013.01); G06F 9/45533 (2013.01); G06F 2009/45579 (2013.01); G06F 2009/45583 (2013.01); G06F 2009/45587 (2013.01)] | 14 Claims |
|
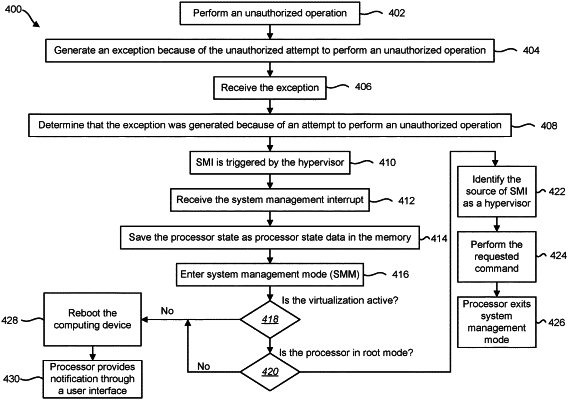
1. A computing device comprising:
memory including a system memory that is accessible during a system management mode of the computing device and inaccessible during a runtime mode of the computing device; and
a processor in electronic communication-with the memory, wherein the processor is to:
receive a system management interrupt;
in response to receiving the system management interrupt, enter the system management mode; and
during the system management mode,
identify trigger code that triggered the system management interrupt received by the processor; and
determine whether the trigger code is virtualization code for protecting the computing device from tampering,
wherein in response to determining that the trigger code is the virtualization code for protecting the computing device from tampering, the processor is to execute a security sensitive command using system code stored in the system memory, and
wherein in response to determining that the trigger code is not the virtualization code for protecting the computing device from tampering, the processor does not execute the security sensitive command.
|