| CPC G06F 21/71 (2013.01) [G06F 8/63 (2013.01); G06F 9/45533 (2013.01); G06F 9/45558 (2013.01); G06F 21/53 (2013.01); G06F 21/57 (2013.01); G06F 21/78 (2013.01); H04L 9/0822 (2013.01); G06F 2009/45579 (2013.01); G06F 2009/45587 (2013.01); G06F 2212/402 (2013.01); G06F 2221/2149 (2013.01)] | 21 Claims |
|
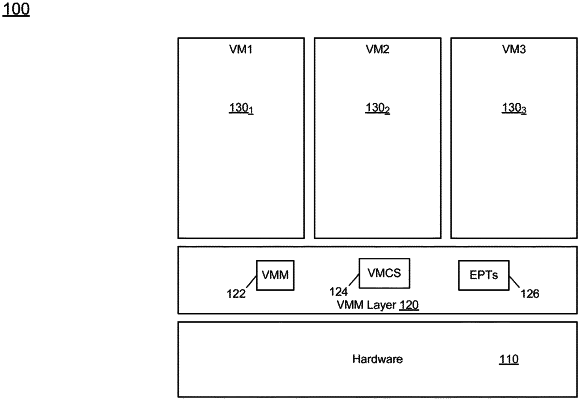
1. At least one non-transitory computer-readable medium comprising instructions that, when executed, cause a processor to facilitate operations comprising:
creating a first key domain, the first key domain comprising a region of a memory to be encrypted by a key domain key;
launching a first guest virtual machine within the first key domain;
intercepting an interrupt;
saving processor register information to a protected location of the memory in response to the interrupt or an exception thrown when the first guest virtual machine causes an exit condition;
clearing a first processor register if the first processor register is not needed by an untrusted host virtual machine monitor managing execution of the first guest virtual machine;
conditionally exposing a second processor register if the second processor register is needed by the untrusted host virtual machine monitor;
invoking the untrusted host virtual machine monitor; and
exiting the first guest virtual machine when the untrusted host virtual machine monitor is invoked.
|