| CPC G06F 21/6272 (2013.01) [G06F 21/602 (2013.01); G06F 21/606 (2013.01); H04L 41/5003 (2013.01); H04L 41/508 (2013.01); G06F 2221/2107 (2013.01)] | 20 Claims |
|
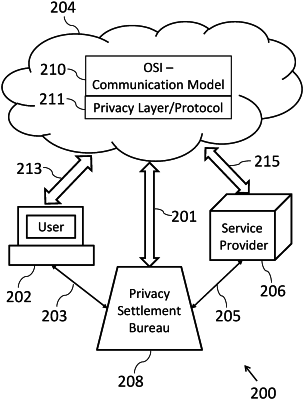
1. A method for privacy policy enforcement to ensure reconciliation between users communicating via an open system interconnection (OSI) communication architecture, the method comprising:
receiving a privacy policy for at least one user's device of a first user;
receiving a usage policy for a user's device of a second user;
modifying the privacy policy by the first user, such that the received usage policy is to allow access to data and content of the at least one user's device of a first user;
receiving by a first server at least one dataset from the first user's device to be sent to the second user's device, wherein the at least one dataset comprises at least one data segment;
encrypting by the first server the received at least one data segment based on received encryption codes;
receiving a privacy policy enforcement vector, having selective decryption keys corresponding to the encryption codes and configured to allow decryption of at least one data segment when a match between the modified privacy policy and the usage policy occurs to decrypt the at least one data segment; and
performing selective decryption, by a second server, for each data segment based on the privacy policy enforcement vector,
wherein at least one of the first server and the second server is external to the first user's device and second user's device, and
wherein the decrypted at least one data segment passes through a privacy layer added to OSI architecture, the privacy layer being in communication with the first user's device.
|