| CPC G06F 21/6263 (2013.01) [G06N 20/20 (2019.01)] | 24 Claims |
|
1. A computer-implemented method, comprising:
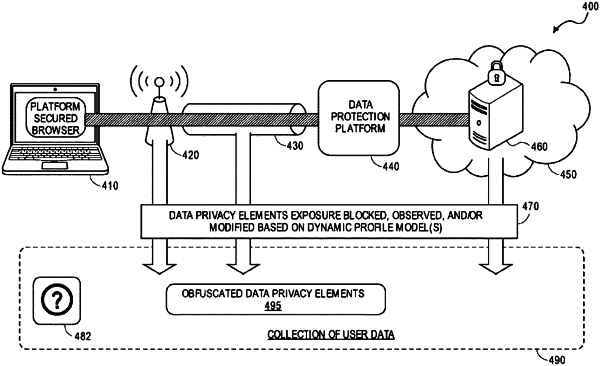
receiving power associated with a primary computing device, wherein the power is received at a data protection device electrically coupled to a power bus implemented on the primary computing device;
detecting one or more data privacy elements associated with a secondary computing device, wherein the one or more data privacy elements identify one or more characteristics associated with operations performable by the secondary computing device, wherein the one or more data privacy elements are detected from a request to access a network location, and are detectable by a network host when accessing the network location, and wherein the request is received over a secure connection between the data protection device and the secondary computing device;
modifying the one or more data privacy elements, wherein modifying the one or more data privacy elements includes replacing the one or more characteristics with inaccurate characteristics associated with the operations performable by the secondary computing device, wherein the inaccurate characteristics are determined based on an output generated by a machine learning model, wherein the output includes one or more attribution vectors, and wherein an attribution vector is determined based on data privacy elements having similar values; and
using the data protection device to transmit the one or more modified data privacy elements, wherein when the network host detects the one or more modified data privacy elements at the network location, the network host accesses the inaccurate characteristics, and wherein the network host accessing the inaccurate characteristics increases a likelihood of the network host being classified as an unauthorized network host.
|