| CPC G06F 21/6245 (2013.01) [G06F 11/3041 (2013.01); G06F 11/3072 (2013.01); G06F 21/60 (2013.01); H04L 63/1425 (2013.01); G06F 11/3006 (2013.01)] | 24 Claims |
|
1. A method comprising:
via processing circuitry communicatively coupled to or integrated with at least one server communicatively coupled to a plurality of client computers:
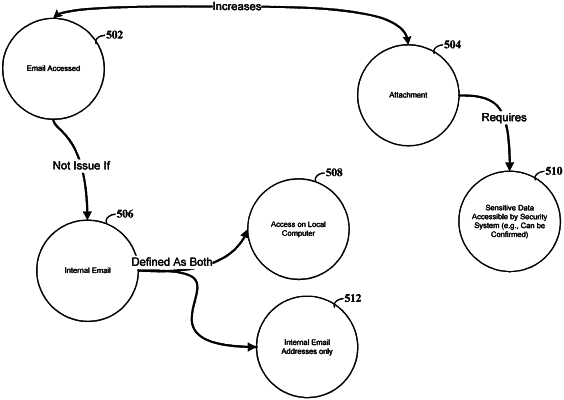
monitoring data communications of one of the plurality of client computers for access of sensitive data by reviewing the data communications related to a notification associated with said one of the plurality of client computers;
performing a security action, based on criteria used to indicate a sensitivity level, selected from among three or more sensitivity levels used by the processing circuitry, of the sensitive data and in response to information received from one or more of the plurality of client computers indicating an occurrence of first and second trigger events that are related to the received information or to an access of the sensitive data and that involve a clipboard-based copying operation associated with said one of the plurality of client computers; and
applying a learning algorithm that defines parameters for detecting the sensitive data and that adjusts a list of one or more approved locations, which are correlated with certain types of data associated with the three or more sensitivity levels, to protect the sensitive data from being sent to a location not in the list.
|