| CPC G06F 21/577 (2013.01) [G06F 8/71 (2013.01); G06F 9/44505 (2013.01); G06F 21/51 (2013.01); G06F 21/552 (2013.01); G06F 21/554 (2013.01); G06F 21/566 (2013.01)] | 4 Claims |
|
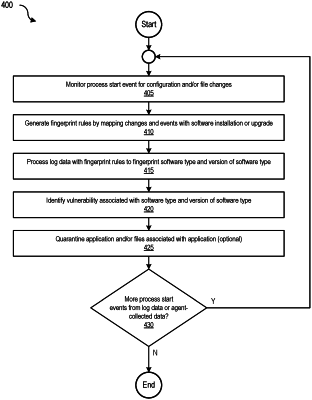
1. A computer-implemented method, comprising:
monitoring a process start event associated with an application for a configuration change or a file change;
generating a fingerprint rule by mapping the configuration change or the file change with a software installation or a software upgrade;
processing log data with the fingerprint rule to fingerprint a software type and a version of the software type;
identifying a vulnerability associated with the software type and the version of the software type;
identifying a binary location of the process start event;
determining the software type and the version of the software type based on the binary location of the process start event;
accessing a record of previously processed binaries;
determining if a binary in the binary location is part of the record; and
inhibiting processing of the binary in the binary location if the binary in the binary location is part of the record.
|