| CPC G06F 21/577 (2013.01) [G06N 5/02 (2013.01); G06F 2221/034 (2013.01)] | 20 Claims |
|
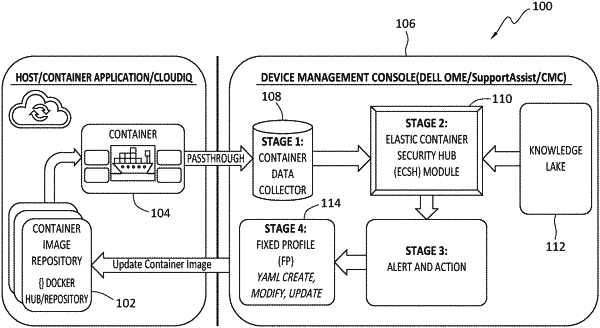
1. A method, comprising the operations:
collecting container information concerning a container with port information of communication undertaken by the container;
analyzing the container information and the port information to identify a security tool needed to perform a vulnerability scan of the container;
accessing the security tool from a knowledge lake;
running the security tool on the container information to identify a security vulnerability of the container;
based on the running of the security tool, generating an alert indicating that the container has the security vulnerability;
capturing the security vulnerability; and
based on the captured security vulnerability, updating a container image that was used to spawn the container.
|