| CPC G06F 21/575 (2013.01) [G06F 2221/034 (2013.01)] | 16 Claims |
|
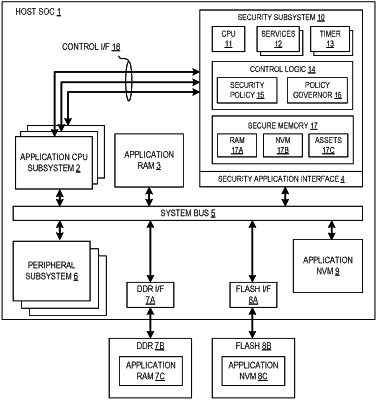
1. A method for securely controlling operations of a data processing system, comprising:
activating a hardware security subsystem to provide security services according to an adjustable set of system security policies, comprising initializing, using immutable software, the hardware security subsystem during bootup of the data processing system to verify a bootloader before starting any other subsystem;
receiving, at the hardware security subsystem, a security service request from an external application subsystem, wherein the security service request includes a confirmation message that an application image was successfully installed and verified upon execution of bootloader firmware, and the security service request is a request for a cryptographic operation to be performed by the hardware security subsystem using a cryptographic key stored in a secure memory that is protected by the hardware security subsystem, where the cryptographic operation is selected from data verification, data encryption, data decryption, performance of a signing operation, data authentication, and creation of a message authentication code;
evaluating, by the hardware security subsystem, the security service request against the adjustable set of system security policies to determine whether the security service request is granted access to the cryptographic key, where the adjustable set of system security policies includes a key usage security policy indicating a permission to access the cryptographic key to perform the cryptographic operation;
generating, at the hardware security subsystem, a response to the security service request using the cryptographic key in response to the security service request being granted access to the cryptographic key;
after performing the cryptographic operation, adjusting, at the hardware security subsystem, the key usage security policy for the cryptographic key by performing a permission removal process on the key usage security policy to remove the permission for the external application subsystem to access the cryptographic key for the cryptographic operation,
wherein the permission removal process is selected from a group consisting of
removing a permission for the external application subsystem to verify data using the cryptographic key,
removing a permission for the external application subsystem to encrypt data using the cryptographic key,
removing a permission for the external application subsystem to decrypt data using the cryptographic key,
removing a permission for the external application subsystem to perform a signing operation using the cryptographic key, and
removing a permission for the external application subsystem to create a message authentication code using the cryptographic key; and
sending the response from the hardware security subsystem to the external application subsystem.
|