| CPC G06F 21/566 (2013.01) [G06F 2221/034 (2013.01)] | 24 Claims |
|
1. A method comprising:
executing, by a computer system, a program in a first mode of operation in a controlled environment in accordance with a normal operation without malicious behavior;
generating, by the computer system, a record of events comprising a plurality of sequences of events that occur during the normal operation of the program;
generating, by the computer system using the record of events, an acceptable behavior model that is indicative of normal behavior of flow control, flow status, or data flow of actions performed by the program that occur during the normal operation without the malicious behavior;
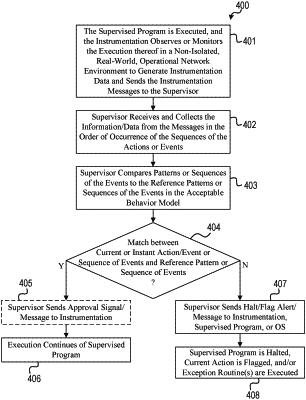
executing, by the computer system, the program in a second mode of operation after the program has been deployed in runtime in a non-isolated, real-world, operational network environment;
determining, by the computer system, an operational sequence of events of the program during execution of the program in the second mode of operation, the operational sequence of events including a current action;
comparing, by the computer system, the operational sequence of events with the acceptable behavior model;
when the comparing step results in a match between the operational sequence of events and the acceptable behavior model, performing the current action in the second mode of operation; and
when the comparing step does not result in the match between the operational sequence of events and the acceptable behavior model, not performing the current action and generating an alert to stop the executing of the program.
|