| CPC G06F 21/565 (2013.01) [G06F 21/567 (2013.01); H04L 63/14 (2013.01); H04L 63/145 (2013.01); G06F 2221/033 (2013.01)] | 20 Claims |
|
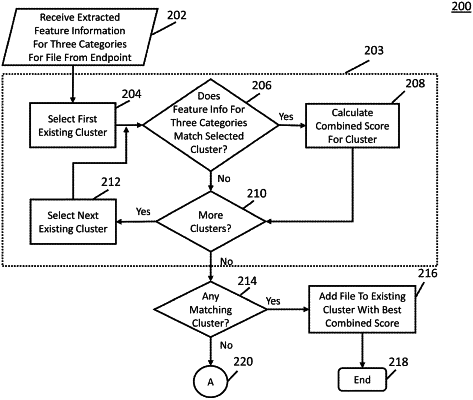
8. A method for identifying and responding to malicious files having similar features, comprising:
receiving, at a hardware processor, feature information extracted from a file, wherein the feature information includes at least two of static feature information, environmental feature information, and behavioral feature information;
for each cluster of a plurality of clusters of files:
for a first portion of the feature information corresponding to one of the static feature information, the environmental feature information, and the behavioral feature information:
determining a first number of features in the first portion of the feature information that match the cluster; and
determining a first score based on a ratio of the first number of features and a total number of features in the first portion of the feature information;
for a second portion of the feature information corresponding to another of the static feature information, the environmental feature information, and the behavioral feature information:
determining a second number of features in the second portion of the feature information that match the cluster; and
determining a second score based on a ratio of the second number of features and a total number of features in the second portion of the feature information; and
determining a combined score for the cluster based on a combination of at least the first score and the second score, wherein the combined score is one of a plurality of combined scores;
identifying one of the plurality of clusters with a best of the plurality of combined scores as matching the file;
determining, using the hardware processor, that the file is malicious; and
reporting to a plurality of endpoints that other files corresponding to the one of the plurality of clusters is malicious.
|