| CPC G06F 21/54 (2013.01) [G06F 21/51 (2013.01); G06F 21/554 (2013.01); G06F 2221/033 (2013.01)] | 27 Claims |
|
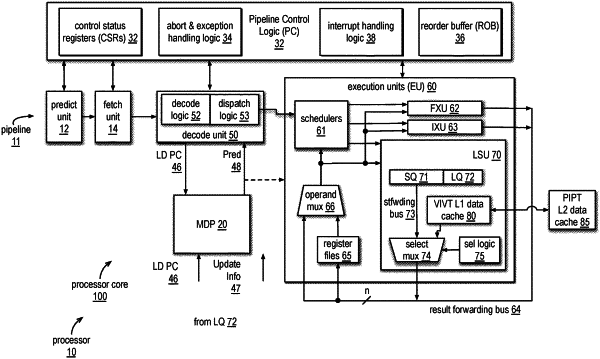
1. A method of mitigating side channel attacks (SCAs) that exploit speculative store-to-load forwarding in a high-performance processor, the method comprising:
conditionally performing speculative store-to-load forwarding (STLF) of data between a load instruction and an uncommitted older store instruction in an execution pipeline;
wherein a first condition of said conditionally performing speculative STLF is a verification that a complete physical data address of the load instruction matches a complete physical data address of the store instruction;
wherein the processor is high-performance in that it is a superscalar, out-of-order, and speculative executing processor; and
wherein said verification mitigates SCAs that exploit speculative store-to-load forwarding by:
speculatively executing a first load instruction that does not have permission to access a secret value at the load instruction's data address;
generating a second address that is a function of the secret value, wherein the function maps the second address to one of 2″ lines of a cache, where n is an integer;
speculatively executing a second load instruction that loads an arbitrary value located at the second address; and
probing the cache to determine where in the cache the arbitrary value was stored, thereby revealing the secret value.
|