| CPC H04L 9/50 (2022.05) [G06Q 20/3674 (2013.01); G06Q 20/3825 (2013.01); G06Q 20/3829 (2013.01); H04L 9/30 (2013.01); H04L 67/1097 (2013.01)] | 19 Claims |
|
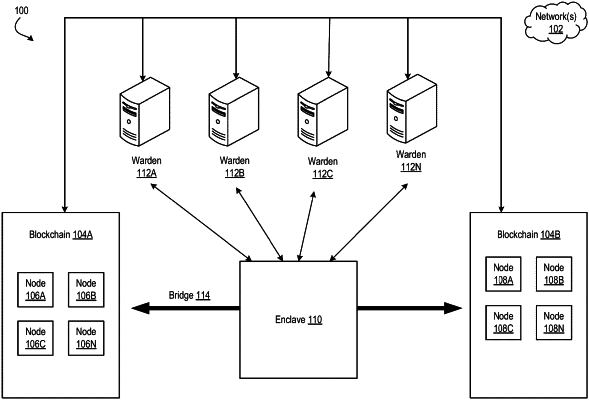
1. A system to bridge assets between blockchain networks, the system comprising:
a secure module configured to:
provide a trusted computing environment within which processing of programs is secure from observation and manipulation by other operations outside of the secure module;
load a bridge program from memory outside the secure module into secure memory within the secure module; and
execute the bridge program within the secure module such that the executing bridge program is secure from observation and manipulation by other operations outside of the secure module, the bridge program comprising instructions that, when executed by the secure module in a particular configuration, cause the secure module to perform operations comprising:
accessing a first blockchain network that records transactions of first assets;
accessing a second blockchain network that records transaction of a second asset;
locking some of the first assets of the first blockchain network and correspondingly minting some of the second assets of the second blockchain network; and
unlocking the locked first assets of the first blockchain network in response to removal of the minted second assets of the second blockchain network; and
remote warden systems that are each configured to maintain a secret share of secret data for the bridge program to lock the first assets and to mint second assets, wherein the secret shares maintained by each of the remote warden systems are configured to be used in combination to regenerate a private key;
wherein each of the remote warden systems are further configured to:
store a portion of a pool of shared secrets that, collectively, are capable of being used to instantiate a new instance of the bridge program,
responsive to a determination that a first instance of the bridge program fails, to provide the portion of the pool of shared secrets to a second instance of the bridge program upon instantiation; and
provide the portion of the pool of shared secrets to the second instance of the bridge program in response to the second instance of the bridge program being validated using an attestation operation by the remote warden systems.
|