| CPC H04L 9/321 (2013.01) [G06F 16/2379 (2019.01); H04L 9/085 (2013.01); H04L 63/1425 (2013.01)] | 19 Claims |
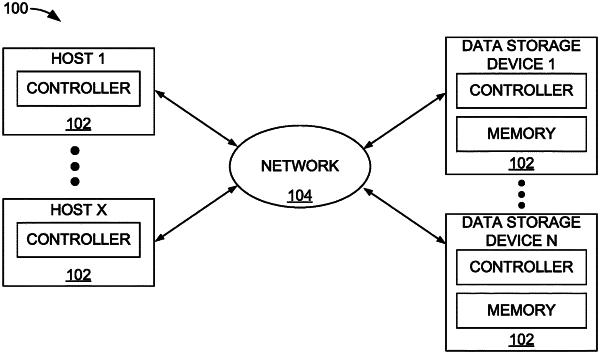
|
1. A method, comprising:
deploying a decentralize module of a distributed computing system, the distributed computing system comprising a system component connected to a host, the system component assigned with an initial reputation score stored on a private ledger accessed by the decentralize module, the initial reputation score based on a characteristic of the system component;
positioning, by the decentralize module and based on the initial reputation score, the system component in a hierarchical device organization, the hierarchical device organization maintained by the decentralize module;
adjusting, by the decentralize module, the initial reputation score and position of the system component in the hierarchical device organization based on a behavior or operational aspect of the system component, recording the adjusted initial reputation score on the private ledger;
generating, by the decentralize module, a decentralized secret sharing scheme, the decentralized secret sharing scheme configured to authenticate the system component with multiple different secrets sourced from different system components logically positioned in different hierarchical levels, subsets, or groups of the hierarchical device organization based on respective reputation scores, each hierarchical level, subset, or group of the hierarchical device organization having different responsibilities, assigned by the decentralize module; and
authenticating, using the decentralize module, the host based on the generating,
wherein the behavior or operational aspect of the system component comprises at least one of a time without a malicious threat, a time without an attack to the system component, a malicious threat to the system component, or an attack to the system component.
|