| CPC H04L 9/0825 (2013.01) [H04L 9/0866 (2013.01); H04L 9/14 (2013.01); H04L 12/4641 (2013.01)] | 18 Claims |
|
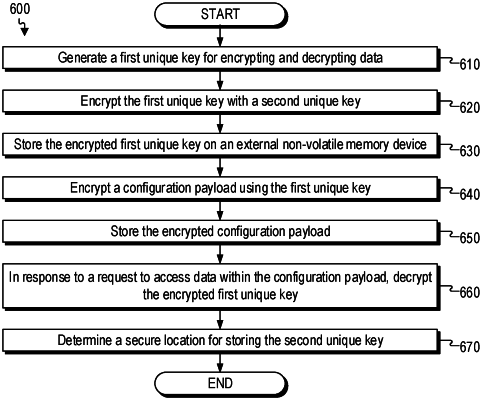
1. A method comprising:
during a boot sequence of a network device, generating a first unique key for encrypting and decrypting data;
encrypting the first unique key with a second unique key to determine an encrypted first unique key;
storing the encrypted first unique key on an external non-volatile memory device;
encrypting a configuration payload with the first unique key;
storing the encrypted configuration payload on an internal non-volatile memory device;
in response to a request to access data within the configuration payload, decrypting the encrypted first unique key using the second unique key and decrypting the encrypted configuration payload using the first unique key;
authenticating the network device by performing a security check on each component of a plurality of different types of components of the network device;
in response to the authenticating of the network device, identifying, a secure location in the network device for storing the second unique key, wherein the secure location is one of the plurality of different types of components of the network device;
and storing the second unique key in the secure location that is accessible to the network device after authentication of the network device.
|