| CPC H04L 9/0643 (2013.01) [G06F 21/64 (2013.01)] | 9 Claims |
|
1. A method for securing data using blockchain technology, realized in a system comprising a central server and two or more subsystems, each of them controlled by a dedicated sub-server, wherein each of the two or more subsystems comprises:
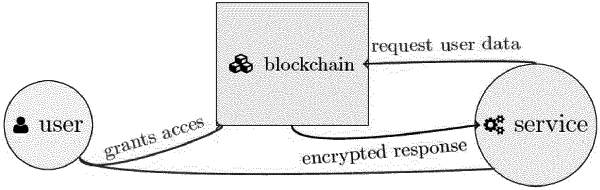
a first blockchain database for storing information data, especially data of biotechnological laboratories, wherein transactions in the first blockchain database are committed according to blockchain rules, including treating a first specific piece of information as a transaction, creating a digital signature of the transaction by an author of said first specific piece of information with the author's digital key, combining transactions into a first new block, encrypting the first new block with a hash of a previous block in the first database and storing the first new block in the first database,
a second blockchain database for storing access data, including digital keys of users having access to the first database and information about permissions to read data from or write data to the first database by each such user associated with the digital key of this user, in which second database information is stored according to blockchain rules, including treating a second specific piece of information as a transaction, creating a digital signature of the transaction by the author of said second specific piece of information with the author's digital key, combining transactions into a second new block, encrypting the second new block with a hash of the previous block in the second database and storing the second new block in the second database,
wherein every authorized user having access to the first database is able to allow another user to read from the first database the data authored by said authorized user by adding the digital key of said another user with information of corresponding permission to said second database,
wherein every authorized user having access to the first database is able to forbid another user to read from the first database the data authored by said authorized user by adding the digital key of said another user with information of corresponding permission to said second database,
wherein every authorized user having access to the first database is able to revoke from another user previously granted rights regarding access to data in the first database authored by said authorized user,
wherein said method for securing data includes verification by the central server of compatibility and immutability of the first and second blockchain databases in said two or more subsystems by:
collecting hashes and optionally timestamps from the first and second blockchain databases in each of said two or more subsystems,
exchanging new transactions between the central server and the sub-servers exchange and independently verifying compatibility of hashes, with the use of the private key of the sub-server to avoid fake hashes;
wherein the central server periodically communicates with the first or second blockchain databases in each of the two or more subsystems, each of the two or more subsystems controlled by a dedicated sub-server, the first or second blockchain databases being periodically verified by the central server; and
wherein the central server is a laboratory server or a central computer without internet access.
|