| CPC H04L 63/1441 (2013.01) [H04L 9/002 (2013.01); H04L 9/32 (2013.01); H04L 63/0272 (2013.01); H04L 63/1408 (2013.01); H04L 63/1416 (2013.01)] | 24 Claims |
|
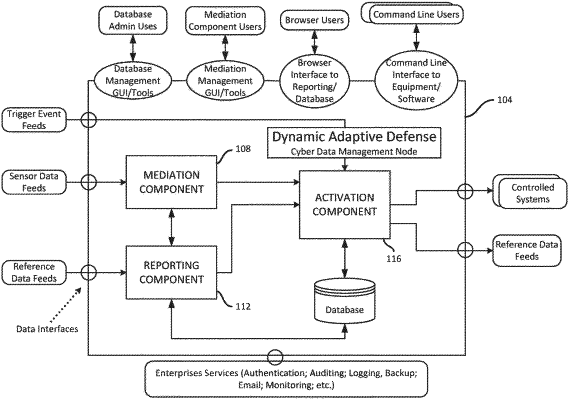
1. At least one non-transitory computer readable medium comprising instructions that, when executed, cause processor circuitry to at least:
map a security threat to at least one action to remediate the security threat, the at least one action previously identified as authorized for an administrator to initiate;
access information from the administrator that correlates a second network security action with a network security element, the second network security action not correlated with the network security element prior to the accessing of the information from the administrator, the information not instructing the execution of the at least one action; and
send, subsequent to the access of the information, a signal to initiate an execution of the second network security action to the network security element.
|