| CPC H04L 63/1425 (2013.01) | 20 Claims |
|
1. A system comprising:
one or more processors; and
one or more non-transitory computer-readable media storing instructions that, when executed by the one or more processors, cause the system to perform operations comprising:
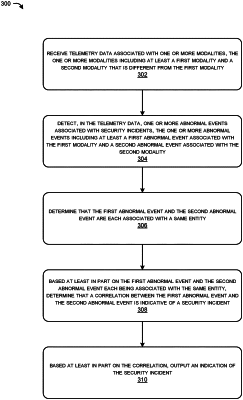
receiving telemetry data associated with one or more modalities, the one or more modalities including at least a first modality and a second modality, the second modality different from the first modality;
detecting, in the telemetry data, one or more abnormal events associated with security incidents, the one or more abnormal events including at least a first abnormal event associated with the first modality and a second abnormal event associated with the second modality;
determining a first mapping between a first endpoint identifier associated with the first modality and a network address associated with an entity;
determining a second mapping between a second endpoint identifier associated with the second modality and the network address associated with the entity;
determining, based at least in part on the first mapping and the second mapping, that the first abnormal event and the second abnormal event are each associated with a same entity;
based at least in part on the first abnormal event and the second abnormal event each being associated with the same entity, determining that a correlation between the first abnormal event and the second abnormal event is indicative of a security incident; and
based at least in part on the correlation, outputting an indication of the security incident.
|