| CPC H04L 63/1425 (2013.01) [H04L 12/40013 (2013.01); H04L 63/0428 (2013.01); H04L 63/1441 (2013.01); H04W 4/44 (2018.02); H04L 2012/40215 (2013.01); H04L 2012/40273 (2013.01)] | 25 Claims |
|
1. A system comprising:
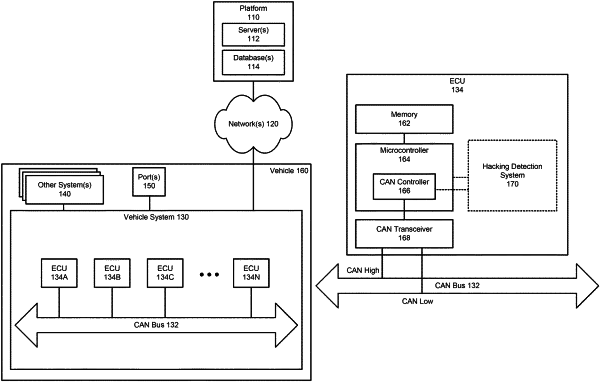
a plurality of electronic control units (ECUs), wherein each of the plurality of ECUs is communicatively connected to a Controller Area Network (CAN) bus within a vehicle, and wherein each of the plurality of ECUs comprises at least one hardware processor and a hacking-detection software module that is configured to, when executed by the at least one hardware processor of the respective ECU,
during an initialization stage,
in accordance with a message protocol, transmit a message comprising a CAN identifier, used by the respective ECU, to at least one other hacking-detection software module on at least one other one of the plurality of ECUs,
in accordance with the message protocol, receive a message comprising a CAN identifier, used by the at least one other ECU, from the other hacking-detection software module,
monitor one or more parameters, including at least one parameter of CAN messages received by the respective ECU and transmitted by the respective ECU, according to a CAN bus protocol, on the CAN bus,
generate a pattern-detection mechanism based on the monitored one or more parameters, and
join at least one peer-to-peer sub-network with one or more other hacking-detection software modules, wherein the at least one peer-to-peer sub-network is associated with a security policy, and wherein each hacking-detection software module that has joined the at least one peer-to-peer sub-network operates in accordance with the associated security policy, and
during a detection stage,
monitor the one or more parameters, and
detect malicious activity based on the generated pattern-detection mechanism and the one or more parameters monitored during the detection stage.
|