| CPC H04L 63/1416 (2013.01) [H04L 63/1425 (2013.01); G06F 16/951 (2019.01); G06N 20/00 (2019.01)] | 18 Claims |
|
1. A method for detecting a credential stealing attack comprising:
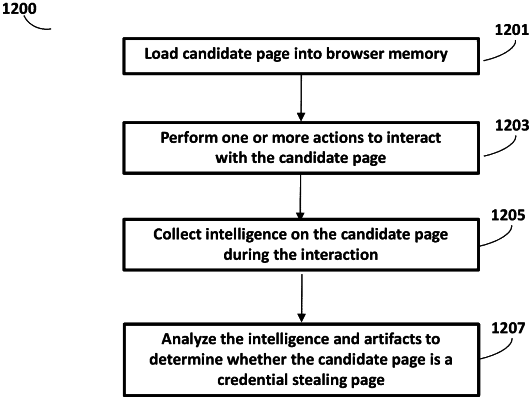
(a) using a page rendering module to i) launch an invisible browser window to load and render a candidate web page into a browser memory by opening an URL of the candidate web page inside the invisible browser window, and ii) extract an artifact from the candidate web page rendered and stored in the browser memory, wherein the artifact comprises image and source code extracted from the browser memory;
(b) extracting, by a custom credential stealing feature extractor, different types of features (i) from the artifact of the candidate web page and (ii) from a known custom credential stealing page to generate a custom similarity feature set;
(c) processing the custom similarity feature set using a machine learning algorithm trained classifier to determine whether the candidate page matches the known custom credential stealing page; and
(d) providing a graphical interface for displaying information regarding the candidate web page, the information comprising: (i) an identity of an infected machine on a network that has accessed the candidate web page if the candidate page matches the known custom credential stealing page and (ii) a feature of the infected machine, wherein the feature is selected from the group consisting of a machine location, a machine usage, a MAC ID, a type of machine, a machine operating system, and an identity of a machine user.
|