| CPC H04L 63/102 (2013.01) [H04L 63/08 (2013.01)] | 20 Claims |
|
1. A method of providing resource access control, the method comprising:
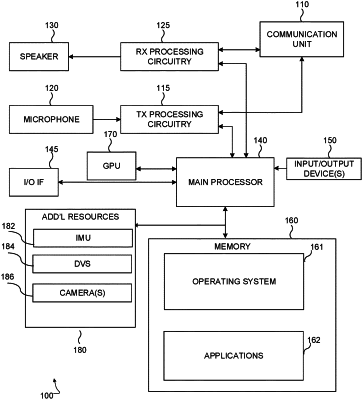
launching, at a boot time, a continuous authentication service for authenticating a user access of a first device, the first device comprising a processor, a memory configured to store a current value of a security state, and one or more sensors configured to collect authentication information;
receiving the authentication information comprising one or more explicit authentication information and one or more implicit authentication information;
performing, by the continuous authentication service, implicit authorization for the one or more implicit authentication information at a time interval scheduled by the continuous authentication service;
updating the current value of the security state based on a response to performing the implicit authorization for the one or more implicit authentication information to generate an updated current value of the security state;
storing the updated current value of the security state in the memory;
sending, via a communication interface, the updated current value of the security state to a second device;
controlling access to a resource of the second device based on the updated current value of the security state;
receiving a request for access to a resource of the first device;
determining, by the continuous authentication service, the updated current value of the security state, the updated current value of the security state based at least in part on a time interval between a receipt time of the authentication information and a current time;
requesting, by the continuous authentication service, the authentication information at a time scheduled by the continuous authentication service;
updating the updated current value of the security state based on a response to requesting the authentication information to generate a twice-updated current value of the security state;
sending, via the communication interface, the twice-updated current value of the security state to the second device; and
controlling access to the resource of the first device and to the resource of the second device based on the twice-updated current value of the security state.
|