| CPC G06Q 20/389 (2013.01) [G06Q 20/02 (2013.01); G06Q 20/401 (2013.01)] | 18 Claims |
|
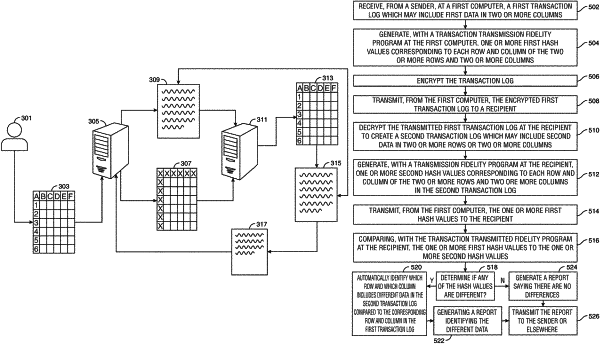
10. A method for detecting transaction transmission fidelity, the method comprising the steps of:
a) receiving, from a sender, at a first computer, a first transaction log comprising (i) first data in two or more rows and two or more columns; and (ii) first metadata;
b) generating, at the first computer, one or more first hash values corresponding to each row and column of the two or more rows and two or more columns;
c) encrypting, at the first computer, the first transaction log;
d) transmitting, from the first computer and via a computer network, the encrypted first transaction log to a recipient;
e) decrypting the transmitted first transaction log at the recipient to create a second transaction log comprising second data in two or more rows and two or more columns;
f) generating, at the recipient, one or more second hash values corresponding to each row and column of the two or more rows and two or more columns in the second transaction log;
g) transmitting, from the first computer, the one or more first hash values to the recipient;
h) comparing, through an artificial intelligence/machine learning algorithm at the recipient, the one or more first hash values to the one or more second hash values; and
i) when one or more of the one or more first hash values are different than any of the corresponding one or more second hash values:
automatically identifying which row and which column comprises different data in the second transaction log compared to the corresponding row and column in the first transaction log;
generating a report identifying the different data;
transmitting the report to the sender;
repairing the second transaction log with the first data to create a repaired second transaction log, wherein the repaired second transaction log is identical to the first transaction log, except for having second metadata, wherein the second metadata is different from the first metadata; and
transmitting the repaired second transaction log to the sender and a second recipient.
|