| CPC G06F 21/602 (2013.01) [G06F 11/1453 (2013.01); G06F 11/1469 (2013.01); H04L 9/0894 (2013.01); G06F 2201/84 (2013.01)] | 16 Claims |
|
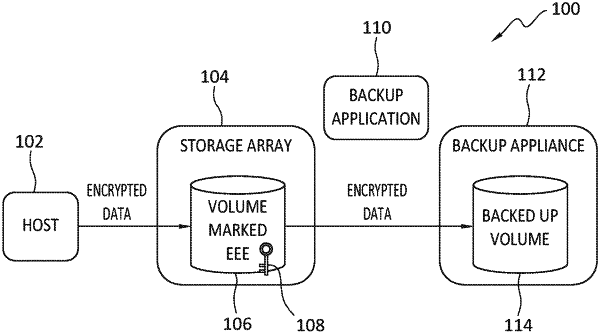
1. A method, comprising:
receiving, by a backup appliance, a dataset for backup from a volume of a storage array;
performing, by the backup appliance, an inquiry to determine if end-to-end encryption is enabled for the volume of the storage array;
receiving, by the backup appliance, confirmation from the storage array that end-to-end encryption is enabled for the volume; and
based on the confirmation that end-to-end encryption is enabled for the volume, storing the dataset in a backup volume without performing encryption, compression, or deduplication, of the dataset prior to storing the dataset in the backup volume.
|