| CPC G06F 21/577 (2013.01) [G06F 2221/034 (2013.01)] | 17 Claims |
|
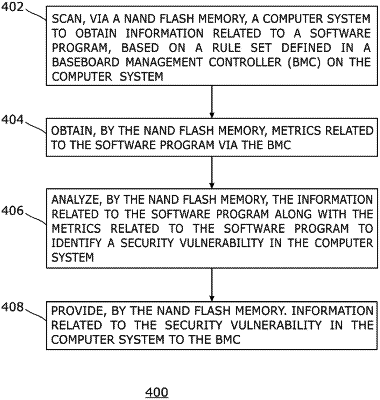
1. A method comprising:
establishing, by a NAND flash memory in a computer system, a communication channel between the NAND flash memory and a software program through a baseboard management controller (BMC), the NAND flash memory being separate from the BMC, and the software program executed on a central processing unit (CPU) separate from the NAND flash memory;
retrieving, by the NAND flash memory, a rule set in the BMC, wherein the rule set includes a parameter to be determined for the software program;
obtaining information related to the software program based on scanning, by the NAND flash memory, the software program over the communication channel through the BMC between the NAND flash memory and the software program, the scanning based on the rule set retrieved by the NAND flash memory from the BMC, wherein the information related to the software program comprises the parameter, and the parameter comprises one or more of a version of the software program on the computer system, a patch applied to the software program, a port related to the software program, a protocol related to the software program, or a service related to the software program;
obtaining, by the NAND flash memory, metrics related to the software program via the BMC;
analyzing, by the NAND flash memory, the information comprising the parameter along with the metrics related to the software program to identify a security vulnerability that is an exploit in the computer system that may be used to perform an unauthorized action within the computer system; and
providing, by the NAND flash memory, information related to the security vulnerability in the computer system to the BMC.
|