| CPC G06F 21/566 (2013.01) [G06F 9/54 (2013.01); G06N 20/00 (2019.01); G06F 2221/034 (2013.01)] | 17 Claims |
|
1. A method for privilege escalation monitoring comprising:
initiating a learning mode;
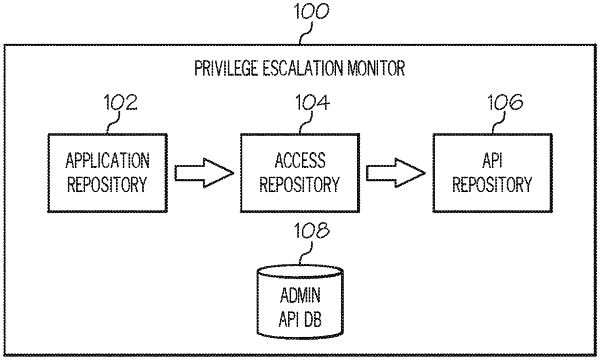
recording application attributes of one or more applications on a host system to an application repository;
recording process attributes of one or more running processes on the host system to an access repository;
recording application programming interface (API) calls of the one or more running processes on the host system to an API repository;
terminating the learning mode;
initializing a protecting mode;
identifying running processes on the host system based on records in the application repository by:
determining whether a process is running on the host system;
determining whether a set of process attributes, belonging to the process, matches a record in the application repository, wherein application attributes includes a name, a hash, a process right, a canonical path, a DLL, or combinations thereof;
generating an alert, in response to determining that the process is not running on the system, the set of process attributes does not match a record in the application repository, or combinations thereof;
enumerating a set of API calls originating from the process, in response to determining that the process is running on the system and the set of process attributes matches a record in the application repository; and
determining whether the process ran with an administrator privilege in the learning mode based on the matched record in the application repository;
determining whether the identified running processes have system access violations based at least in part on the application repository;
determining whether the identified running processes have file permission escalations based at least in part on the access repository;
determining whether the identified running processes have failed privileged API calls based at least in part on the API repository;
generating an alert, in response to determining that the identified running processes have system access violations, file permission escalations, failed privileged API calls, or combinations thereof; and
terminating an offending process corresponding to the alert.
|