| CPC G06F 21/565 (2013.01) [G06F 16/2365 (2019.01)] | 19 Claims |
|
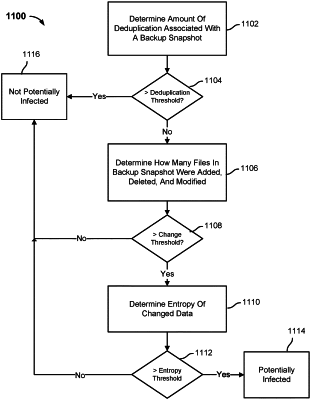
1. A method, comprising:
determining an amount of deduplication associated with a backup snapshot;
in response to determining that the amount of deduplication associated with the backup snapshot is less than a deduplication threshold, determining a number of files associated with the backup snapshot that were added, deleted, and/or modified;
in response to determining that the number of files associated with the backup snapshot that were added, deleted, and/or modified is greater than a change threshold, determining an amount of entropy associated with changed data included in the backup snapshot, wherein the entropy associated with the changed data is a measure of randomness associated with a file;
in response to determining that the amount of entropy associated with changed data included in the backup snapshot is greater than an entropy threshold, determining that the backup snapshot is potentially infected with malicious software; and
providing to a primary system a notification that the backup snapshot includes data that is potentially infected with malicious software.
|