| CPC G06F 21/41 (2013.01) [H04L 63/0815 (2013.01); H04L 63/0823 (2013.01); H04L 63/083 (2013.01)] | 20 Claims |
|
1. A method for execution on a computing system, the method comprising:
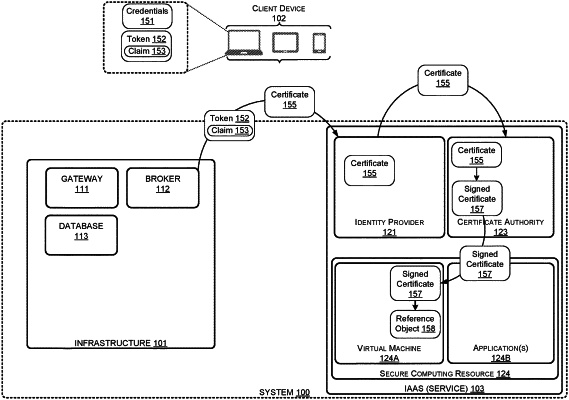
receiving, at an identity provider executing on the computing system, a set of credentials from a client device, wherein the client device is separate from the computing system;
generating, at the identity provider, a token indicating validity of the set of credentials in response to determining that the set of credentials meets one or more criteria, the token defining a claim for a single sign-on flow for a user associated with the set of credentials;
communicating the token to the client device from the computing system, wherein the client device is configured to communicate the token with a request to a broker to initiate the single sign-on flow for accessing a secure computing resource of a service executing at the computing system;
receiving, at the broker, the request from the client device for access to the secure computing resource of the service, wherein the request comprises the token that defines the claim for the single sign-on flow for the user associated with the set of credentials;
in response to determining that the request comprises the token and the claim generated by the identity provider, causing the secure computing resource at the service to generate an unsigned certificate from the token, wherein the secure computing resource is configured to communicate the unsigned certificate and the token defining the claim to the identity provider;
causing the identity provider at the secure computing resource to verify the token and to send the unsigned certificate to a certificate authority at the secure computing resource to generate a signed certificate from the unsigned certificate, wherein the certificate authority comprises security data provided by the user to sign the unsigned certificate; and
sending the signed certificate to the secure computing resource, where the signed certificate enables the client device to access the secure computing resource through a connection without requiring the client device to resubmit the set of credentials, and without requiring the secure computing resource to generate another unsigned certificate for accessing the secure computing resource.
|