| CPC H04L 9/50 (2022.05) [H04L 9/008 (2013.01); H04L 9/0618 (2013.01); H04L 9/3073 (2013.01)] | 6 Claims |
|
1. A searchable encrypted data sharing method based on blockchain and homomorphic encryption, comprising the following steps:
a) performing system initialization by:
generating relevant system parameters according to security parameters, the system parameters being used to generate a public-private key pair of a user, identity verification and consistency verification; and defining a keyword set, which is used for the consistency verification of on-chain transaction; and
when the user joins an alliance chain, a cloud server assigning an identity identification to the user, and the user generating the public-private key pair and makes his/her public key open, the cloud server signing the user's identity by using the user's public key, a public key of an alliance chain manager, and its own private key, and uploading it to an alliance chain network;
b) performing data release by:
a data owner encrypting his sensitive data and keywords corresponding to the sensitive data, and sending ciphertext of the sensitive data, ciphertext of the keyword, his/her own identity information and proof of consistency to the cloud server;
the cloud server verifying the identity of the data owner; if the verification succeeds, the sensitive data being stored in a local server, and a ciphertext index value of the sensitive data, the ciphertext of the keyword, and the proof of consistency being sent to the alliance chain; and
after the alliance chain receives the data uploaded by the cloud server, it verifying the consistency of the message; if the verification is passed, the pseudo-identity information of the data owner, the ciphertext index value of the sensitive data and the ciphertext of the keywords being stored in the alliance chain;
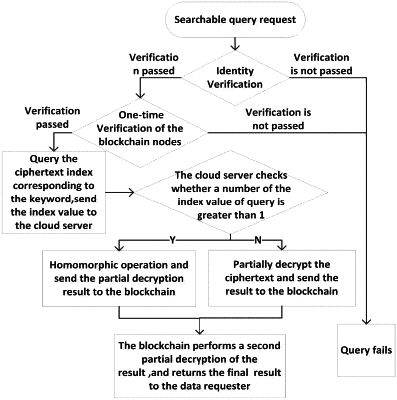
c) performing a data request by:
a data requester generating a trapdoor function of the keyword, and sending the trapdoor function to the manager in the alliance chain;
after receiving the request, the manager verifying the identity information of the data requester; if the verification is passed, performing search operation, and sending the ciphertext index value of the found sensitive data to the cloud server;
the cloud server receiving the ciphertext index value of the sensitive data; if the number of index values is 1, a partial decryption operation being performed on the ciphertext of the sensitive data, and the partially decrypted ciphertext being sent to the manager; the manager then performing partial decryption on the data again, and returning a final decryption result to the data requester; and
if the number of index values is greater than 1, performing a homomorphic operation on the ciphertext set, and then partially decrypting the ciphertext result after the homomorphic operation, and finally sending the partial decryption result to the manager; the manager using his own private key to perform partial decryption after receiving the partially decrypted ciphertext set, and returning the final decryption result to the data requester; and
d) performing data acquisition by:
the data requester obtaining the converted ciphertext data, decrypting it with his own private key to obtain a plaintext message, so as to obtain the sensitive data related to the searched keywords.
|