| CPC H04L 9/0858 (2013.01) [H04L 9/0861 (2013.01); H04L 9/14 (2013.01); H04L 9/3236 (2013.01)] | 20 Claims |
|
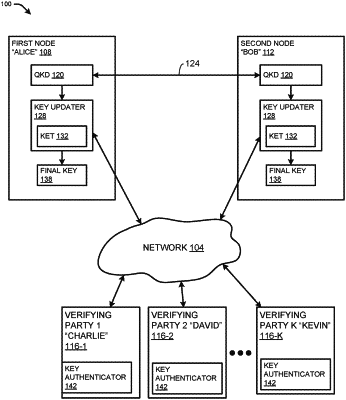
1. A non-transitory machine readable medium having machine executable instructions comprising a key updater for a first party operating on a network that:
generates a mutually distilled key for communication between the first party and a second party;
determines a set of verifying parties operating on the network needed to authenticate the mutually distilled key, wherein each verifying party of the set of verifying parties operates on the network;
iteratively executes a key equivalency test for each verifying party in the set of verifying parties to determine a nonce sum until the key equivalency test has been executed for each of the verifying parties in the set of verifying parties or until it is determined that at least one node on the network has been compromised; and
generates a final key for communication between the first party and the second party based on the nonce sum and the mutually distilled key if the key equivalency test was successfully executed for each verifying party of the set of verifying parties.
|