| CPC H04L 9/083 (2013.01) [G06F 21/316 (2013.01); G06F 21/602 (2013.01); G06F 21/62 (2013.01); H04L 9/0819 (2013.01); H04L 9/0822 (2013.01); H04L 9/0861 (2013.01); H04L 63/04 (2013.01); H04L 63/0428 (2013.01); H04L 63/062 (2013.01); H04L 63/065 (2013.01); H04L 63/0815 (2013.01); H04L 63/10 (2013.01); H04L 63/102 (2013.01); G06F 2221/2113 (2013.01); G06F 2221/2133 (2013.01)] | 20 Claims |
|
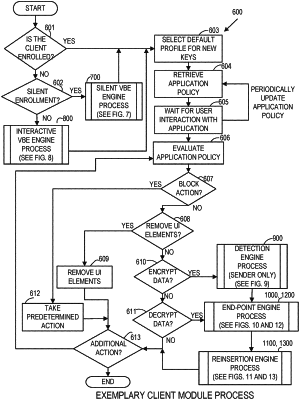
1. A method, comprising:
receiving, via at least one computing device, at least one policy for enabling cryptographically secure tracking of electronic activities of a user and a particular electronic computing device, wherein the at least one policy comprises definitions for a plurality of actions to be taken with respect to certain electronic activities resulting from interaction by the user with the at least one computing device;
identifying, via the at least one computing device, a particular electronic activity resulting from user interaction with the at least one computing device;
determining, via the at least one computing device, a particular action to take by applying the at least one policy to the particular electronic activity;
initiating, via the at least one computing device, the particular action with respect to the particular electronic activity; and
suppressing, via the at least one computing device, the user interaction with an intended application by performing the particular action comprising removing one or more user interface elements from the intended application.
|