| CPC H04L 63/102 (2013.01) [H04L 9/3236 (2013.01); H04L 63/08 (2013.01); H04L 2463/082 (2013.01)] | 20 Claims |
|
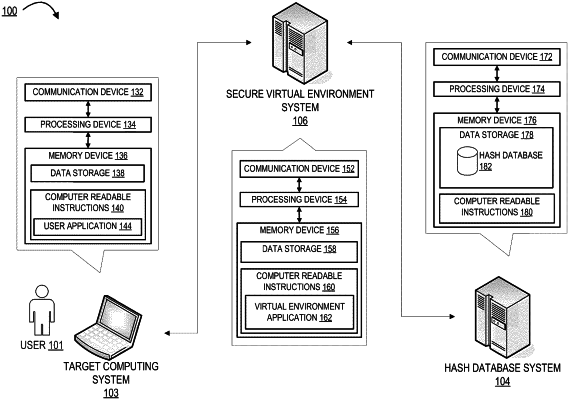
1. A system for improving security of networks using environment hashes, the system comprising:
one or more memory devices storing computer-readable code; and
one or more processing devices operatively coupled to the one or more memory devices, wherein the computer-readable code is configured to cause the one or more processing devices to:
receive a request from an entity to access a network through the use of an entity computer system;
receive authentication credentials from the entity;
compare the authentication credentials from the entity with authentication requirements;
identify an environment hash for the entity computer system, wherein the environment hash comprises a cryptographic hash output value, wherein identifying the environment hash comprises accessing a shared hash database comprising a plurality of environment hashes for a plurality of entity computer systems and identifying the environment hash for the entity computer system, wherein the shared hash database is populated with the plurality of environment hashes from a plurality of third party entities, and wherein the plurality of environment hashes comprise authorized environment hashes and unauthorized environment hashes;
compare the environment hash for the entity computer system with hash requirements; and at least one of:
allow the entity computer system to access the network when the entity computer system is validated based on the comparison of the authentication credentials and the authentication requirements and the comparison of the environment hash and the hash requirements; and
prevent the entity computer system from accessing the network when the entity computer system fails to be validated based on the comparison of the authentication credentials and the authentication requirements or the environment hash and the hash requirements.
|