| CPC H04L 63/10 (2013.01) [G06F 16/9554 (2019.01); G06F 21/53 (2013.01); G06F 21/566 (2013.01); G06F 21/629 (2013.01); G06K 7/1417 (2013.01); H04L 63/02 (2013.01); H04L 63/14 (2013.01); H04L 63/1483 (2013.01); H04W 12/128 (2021.01); G06F 2221/2149 (2013.01); H04L 63/101 (2013.01); H04W 12/77 (2021.01)] | 13 Claims |
|
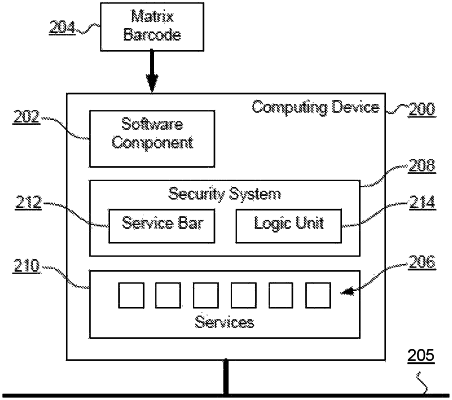
1. A security method for a network-connected computing device, the computing device configured to provide services, the method comprising:
reading information stored in a matrix barcode with a first software component of a plurality of software components executing on the computing device, the information comprising a reference to a resource accessible via the network; and
by a security system operating on the computing device:
blocking the first software component from accessing at least a subset of the services provided by the computing device and allowing the first software component to access at least one of the services provided by the computing device;
determining, based on the information read from the matrix barcode, the services provided by the computing device that are needed by the first software component to access the resource; and
responsive to a verification of permission of the first software component to access the determined services provided by the computing device, unblocking the first software component in order that the first software component accesses the resource and accesses the determined services provided by the computing device.
|