| CPC H04W 12/068 (2021.01) [G06F 21/45 (2013.01); H04L 63/062 (2013.01); H04L 63/083 (2013.01); H04L 63/0884 (2013.01); H04L 63/18 (2013.01); H04L 63/20 (2013.01); H04W 12/069 (2021.01); H04W 12/08 (2013.01); G06F 2221/2149 (2013.01)] | 30 Claims |
|
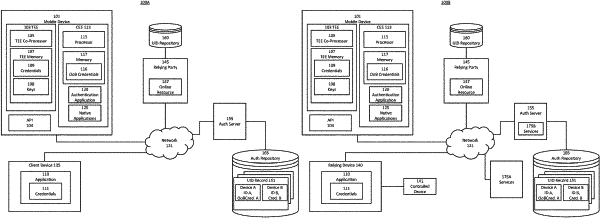
1. A computer-implemented method, comprising:
obtaining a registration value by a first computing device, the registration value corresponding to a second computing device;
transmitting, to a server system, the registration value;
establishing a set of credentials corresponding a user within a memory of the first computing device;
transmitting, to the server system, first data for verifying results of authentication of the user determined by the first computing device;
receiving a request to login the user on the second computing device;
determining, in response to the request, a result of authentication of the user on the first computing device based on obtained input corresponding to the user and the set of credentials; and
transmitting, to the server system, second data indicative of the result of authentication of the user to cause the server system to login the user on the second computing device in response to verification of the second data based on the first data.
|