| CPC H04L 63/105 (2013.01) [G06F 9/45558 (2013.01); H04L 41/22 (2013.01); H04L 63/1433 (2013.01); H04L 63/20 (2013.01); G06F 2009/45587 (2013.01); G06F 2009/45595 (2013.01)] | 20 Claims |
|
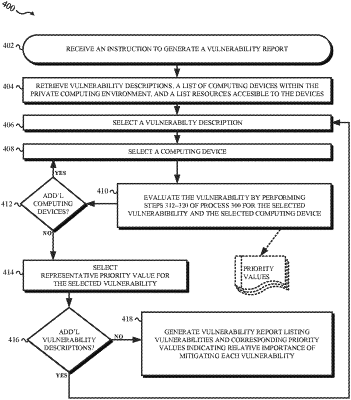
1. A method for evaluating a computing system, the method comprising:
a) selecting, from a list of vulnerability descriptions associated with vulnerabilities, one of the vulnerability descriptions associated with one of the vulnerabilities, the one of the vulnerabilities having a baseline priority score indicative of an estimate of a severity of the one of the vulnerabilities that does not account for mitigating factors or exacerbating factors unique to particular circumstances of the one of the vulnerabilities;
b) selecting, from a list of computing devices operating within a computing environment, one of the computing devices;
c) receiving network configuration information of the computing environment that defines a maximum level of network access to the one of the computing devices, and determining a maximum privilege level allowed for applications executing within the one of the computing devices;
d) converting the maximum level of network access to a system access score according to a predefined vulnerability metric definition, and converting the maximum privilege level to a system privilege score according to the predefined vulnerability metric definition;
e) evaluating, based at least in part on information accessible to the one of the computing devices, the one of the vulnerabilities for the one of the computing devices, including generating a vulnerability priority score for the one of the vulnerabilities with respect to the one of the computing devices by:
converting a level of data sensitivity for the information accessible to the one of the computing devices into a data sensitivity score; and
providing the baseline priority score, the data sensitivity score, the system access score, and the system privilege score as inputs to a weighting function, the weighting function configured to output the vulnerability priority score for the one of the vulnerabilities according to weighting rules of the weighting function;
f) repeating steps b) through e) for additional ones of the computing devices from the list of computing devices;
g) selecting or generating, from the vulnerability priority scores generated in step e), a representative vulnerability priority score indicating an aggregate vulnerability priority score for the one of the vulnerabilities with respect to the computing devices;
h) repeating steps a) through g) for additional ones of the vulnerability descriptions from the list of vulnerability descriptions; and
i) generating a vulnerability report listing the vulnerabilities corresponding to each vulnerability description and corresponding vulnerability priority score indicating a relative importance of mitigating each vulnerability.
|