| CPC H04L 63/0272 (2013.01) [G06F 16/22 (2019.01); H04L 63/029 (2013.01); H04L 63/20 (2013.01)] | 12 Claims |
|
1. A method for improving security and management of information technology by creating an identifiable ecosystem, comprising:
a) configuring at least one database to accept a virtual isolation network registration therein of at least one virtual isolation network including at least one security instance operating at, at least one network security point, the at least one security instance operating with at least one segregated virtual network unit, wherein the at least one segregated virtual network unit utilizes at least one of a shared physical and virtual host kernel, having a fully contained dedicated Layer 2-7 network stack and ability to host applications, the at least one segregated virtual network unit hosting at least one application module;
b) configuring the at least one virtual isolation network to accept a first element registration-of a first element;
c) registering the first element in the at least one database;
d) enabling the registered first element to connect to at least one virtual isolation network via the at least one network security point to the at least one security instance;
e) applying at least one defined security policy for the communication by the first element via the at least one virtual isolation network to at least one of a communication source or destination,
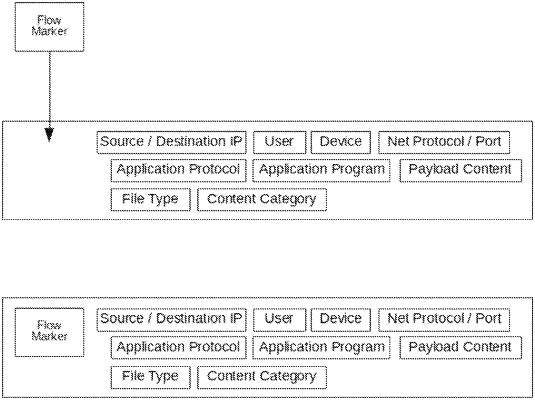
wherein at least one defined security function is applied by the at least one defined security policy using at least one respective flow marker which references the at least one defined security policy to identify if and in what sequence communication through the at least one segregated virtual network unit and at least one application module of the at least one security instance is to be activated,
wherein the at least one element includes at least one of: a user, an electronic device, an IoT device, a network, a cloud network, a physical facility, a cloud instance, a Software-as-a-Service application, a software application, an operating system, a virtual machine, a connected member element, a non-connected member element;
wherein the first element communicates with an at least one additional element within the at least one virtual isolation network but is restricted from communicating beyond the at least one virtual isolation network, and
wherein the at least one security instance is configured to include modular interconnected respective segregated virtual network units.
|