| CPC G06F 21/556 (2013.01) [G06F 21/54 (2013.01); G06F 21/554 (2013.01); G06F 21/87 (2013.01)] | 18 Claims |
|
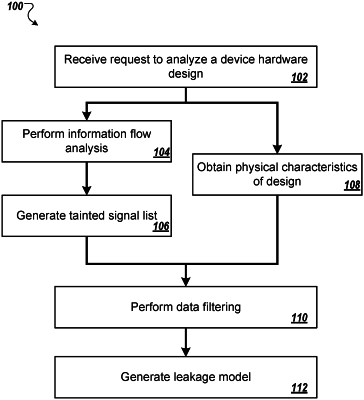
1. A computer-implemented method comprising:
receiving a request to analyze a device hardware design of a device for side-channel vulnerabilities;
obtaining physical characteristics data representing one or more physical characteristics of the device based on the device hardware design;
performing information flow analysis to identify one or more signals of interest corresponding to digital assets;
generating, from the physical characteristics data and the one or more signals of interest, data representing potentially vulnerable signals in the device hardware design including filtering the physical characteristics data of the device by the one or more signals of interest identified by the information flow analysis and by one or more time windows in which a signal of interest is present on one or more structures of the device hardware design; and
generating a leakage model for the potentially vulnerable signals that quantifies one or more leakage criteria for the one or more structures of the device hardware design.
|