| CPC G06F 21/10 (2013.01) [H04L 63/102 (2013.01)] | 14 Claims |
|
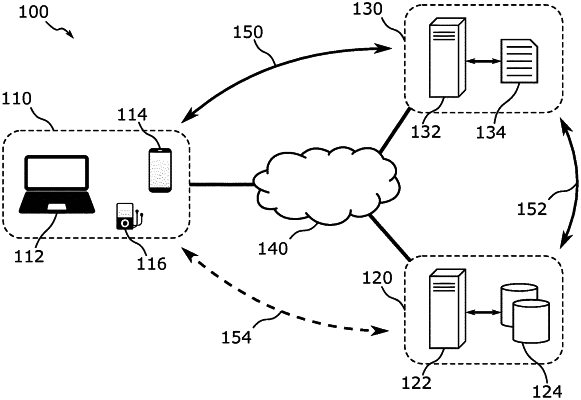
1. A method of providing a media content in a computer network, comprising, in a server system of a media content provider:
a) obtaining a user identification, UID, of a user registered with a partner of the media content provider, and a content identification, CID, of a media content offered by the media content provider;
b) generating a first token associated with the obtained UID and CID;
c) storing the first token in a data storage;
d) providing a reference to a web resource to at least one of the user or to the partner, the reference including a second token equal to, or at least associated with, the first token;
e) receiving a first request from the user to access the web resource, the first request including the second token;
f) providing the web resource to the user, the web resource identifying a network location and including a third token equal to, or at least associated with, at least one of the first token or the second token;
g) receiving a second request from the user to access the network location, the second request including the third token;
h) confirming, based at least on a comparison of the third token with the first token stored in the data storage, whether the user is allowed an access to at least part of the media content; and
i) if confirming in step h) that the user is allowed the access, providing at least part of the media content to the user;
wherein the method further comprises obtaining, before step h), an indication from the partner on whether the user is allowed the access and invalidating or removing the first token in/from the data storage if it is indicated that the user is not allowed the access.
|