| CPC A63F 13/75 (2014.09) [A63F 13/71 (2014.09); A63F 13/79 (2014.09); G06F 21/64 (2013.01); G06N 3/006 (2013.01); A63F 2300/5586 (2013.01); A63F 2300/575 (2013.01)] | 22 Claims |
|
1. A system for identifying whether an object has been modified in a virtual environment, the system comprising:
a server computer in communication with one or more client computers, the server computer configured to:
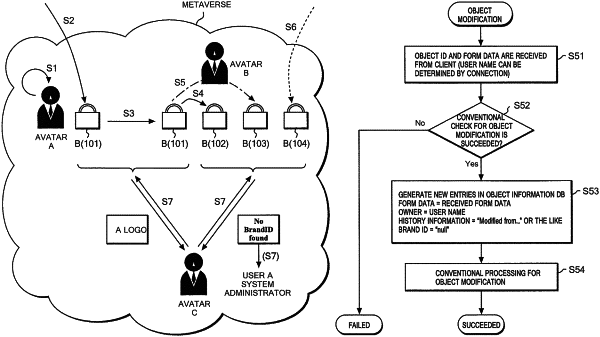
store information about the object in the virtual environment, wherein the information comprises at least a unique ID and authenticity data;
process a modification request from the one or more client computers, wherein the modification request corresponds to the object, wherein processing the modification request modifies the object to form the modified object, and wherein the modification request is processed by storing information corresponding to the modified object together with information corresponding to the object;
process a request for the modified object from the one or more client computers; and
generate authenticity information corresponding to the modified object, wherein the authenticity information indicates the modification of the object.
|