| CPC H04L 9/3247 (2013.01) [H04L 9/3239 (2013.01); H04L 63/0236 (2013.01); H04L 63/0281 (2013.01)] | 1 Claim |
|
1. A judgment method for edge node computing result trustworthiness based on trust evaluation, characterized in that the method comprises following steps:
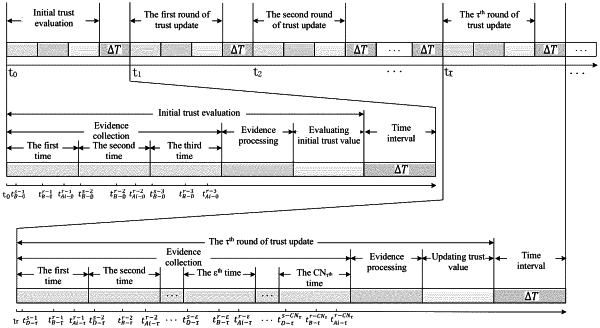
S1 Before Network Operation: each edge node to be added transmits identity information IDAi to an edge proxy for registration, a security administrator sets an error rate ERAi of computing errors allowed to be caused by each edge node in an industrial production environment; the edge proxy marks evidence collected for which number of times with ε (ε=1, 2, . . . , CNτ), and marks trust associated information as a trust value computed in which round with τ (τ∈N), where τ=0 when an initial trust value is evaluated, τ≥1 when a trust value is updated; CNτ represents a total number of times of evidence collection required when the edge proxy computes a trust value in a τth round, and tτ represents time when the edge proxy starts computing the trust value in the τth round; and after verifying an identity of an edge node, the edge proxy starts evaluating an initial trust value of the edge node;
S11 Evidence Collection: the edge proxy starts evaluating the initial trust value of the edge node at t0, the edge proxy randomly generates a to-be-computed data set DataB-0c-ε={a0-0ε, a1-0ε, a2-0ε, . . . , al-0ε}, and generates a result set DataB-0r-ε={b1-0ε, b2-0ε, b3-0ε, . . . , bl-0ε} after adjacent data are pairwise computed as a reference set, wherein this solution specifies that the number of times of evidence collection CN0 required for initial trust value evaluation is 3;
the edge proxy transmits a to-be-computed set to the edge node, the edge node computes and then transmits a computing result set DataAi-0r-ε={c1-0ε, c2-0ε, c3-0ε, . . . , cl-0ε} and a computing result Hash value set DataAi-0r-ε={h1-0ε, h2-0ε, h3-0ε, . . . , hl-0ε} to the edge proxy;
according to the computing result set DataAi-0r-ε from the edge node, the edge proxy computes a Hash value DataAi-0h′-ε={h1-0ε′, h2-0ε′, h3-0ε′, . . . , hl-0ε′} corresponding thereto;
the edge proxy records time tB-0s-ε when the to-be-collected set is transmitted for the ε time, time tB-0r-ε when computing is completed, and time tAi-0r-ε when a computing result of an edge node Ai is received, where i represents a number of nodes, i=1, 2, . . . , n;
S12 Evidence Processing: the edge proxy processes collected data as follows:
(S12-1) accuracy represents a proportion of the number of correct computing results to the number of total data; an accuracy computing formula of evidence collection for the εth time is as follows:
 where NAi-τac-ε represents identical number in a result set DataB-τr-ε computed by the edge proxy in evidence collection for the εth time and a result set DataAi-τr-ε computed by the edge node Ai, ε represents evidence collected for the εth time, τ represents trust computing in the τth round, and l represents a data amount in evidence collection each time;
(S12-2) integrity represents a proportion of the number of complete data to the number of total data; an integrity computing formula of evidence collection for the ϑth time is as follows:
 where NAi-τcm-ε represents identical number in a result Hash value set DataAi-εh′-ε computed by the edge proxy in evidence collection for the εth time and a result Hash value set DataAi-τh-ε computed by the edge node Ai, ε represents evidence collected for the εth time, τ represents trust computing in the τth round, and l represents a data amount in evidence collection each time;
(S12-3) timeliness represents a difference between a computing efficiency of the edge node Ai and a computing efficiency of the edge proxy; a timeliness computing formula of evidence collection for the εth time is as follows:
EAi-τtm-ε=TAi-τtm-ε−TB-τtm-ε (3)
where TAi-τtm-ε represents a computing efficiency of the edge node in evidence collection for the εth time; TB-τtm-ε represents a computing efficiency of the edge proxy in evidence collection for the εth time, and τ represents trust computing in the τth round;
when the edge proxy evaluates the initial trust value, the edge proxy computes a computing efficiency
 of CN0 edge nodes and a computing efficiency
 of the edge proxy according to the time tB-0s-ε when the to-be-collected set is transmitted for εth time, the time tB-0r-ε when computing of the to-be-computed set is completed, and the time tAi-0r-ε when a computing result of an edge node Ai is received, substitutes the results into formula (3), and computes to obtain timeliness of the CN0 edge nodes Ai;
when evaluating the initial trust value, the edge proxy processes evidence collected for three times by means of formula (1), formula (2) and formula (3), to obtain three values of each of accuracy, integrity and timeliness of the edge nodes Ai to be added;
S13 Initial Trust Evaluation:
(S13-1) Computing Initial Trust Value:
a direct trust value is a quantization value that indicates an ability of the edge node to complete a request task and is based on an interactive record history between the edge proxy and the edge node; when the edge proxy computes the initial trust value of the edge node, the edge node is in a to-be-operated state; the edge proxy conducts fuzzy evaluation on direct trust factors of edge nodes to be operated respectively, steps of computing direct trust values are as follow:
(S13-1-a) determining a factor set E={EAi-τac-ε, EAi-τcm-ε, EAi-τtm-ε}, and an evaluation set V={V1, V2, V3}, where V1 represents untrustworthiness, V2 represents uncertainty, and V3 represents trustworthiness; it is stipulated that μun is an untrustworthy membership degree, and 0≤μun<βu; μin is an uncertain membership degree, and βu≤μin<βc; μcr is a trustworthy membership degree, and βc≤μcr≤1, where βu is untrustworthy threshold and βc is trustworthy threshold; the edge proxy computes membership degrees of accuracy, integrity and timeliness, computing formulae are as follows:
S13-1-a-1 computing formula of membership degree of accuracy in evidence collection for the εth time is as follows:
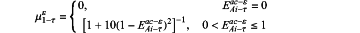 S13-1-a-2 computing formula of membership degree of integrity in evidence collection for the εth time is as follows:
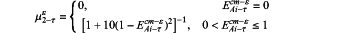 S13-1-a-3 computing formula of membership degree of timeliness in evidence collection for the εth time is
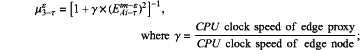 (S13-1-b) computing proportions of membership degrees corresponding to accuracy, integrity and timeliness in trust computing in the τth round belonging to V1, V2, V3, which are {r11-τ, r12-τ, r13-τ}, {r21-τ, r22-τ, r23-τ} and {r31-τ, r32-τ, r33-τ} respectively, for example,
 where N(μ1-τun-ε) represents the number of accuracy membership degrees of CNτ accuracy membership degrees within an untrustworthy membership degree range; the edge proxy obtains a judgment matrix
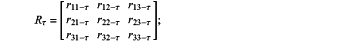 (S13-1-c) computing weight corresponding to accuracy, integrity and timeliness using the entropy weight method, the computing steps being as follows:
S13-1-c-1 forming a matrix by CNτ membership degrees μ1-τε, μ2-τε, μ3-τε corresponding to accuracy, integrity and timeliness:
 S13-1-c-2 computing information entropy corresponding to accuracy, integrity and timeliness:
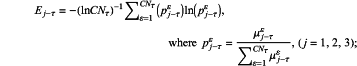 S13-1-c-3 computing weight corresponding to accuracy, integrity and timeliness:
 in order to avoid the condition where the weight is zero when the degree of dispersion of a certain factor is too small, weight ranges corresponding to accuracy, integrity and timeliness are α1∈[0.5,0.8], α2∈[0.01,0.2] and α3∈[0.2,0.4] respectively, where α1>α3>α2; when the weight obtained using the entropy weight method is not within the specified range, the maximum or minimum value of the corresponding range is taken, actual weight is
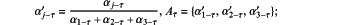 (S13-1-d) computing a judgment result ZAi-τ=Aτ*Rτ={z1-τ, z2-τ, z3-τ}, there being following three cases:
S13-1-d-1 when z1-τ is the maximum, the edge node Ai is untrustworthy, the edge proxy does not compute an average membership degree of accuracy, integrity and timeliness;
S13-1-d-2 when z2-τ is the maximum, the edge node Ai is uncertain in trust, the edge proxy computes means of membership degrees within a range [βu, βc) corresponding to accuracy, integrity and timeliness, which are
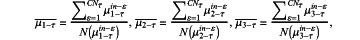 where a denominator represents the number of membership degrees of all factors within the range [βu, βc) and a numerator represents the sum of membership degrees of all factors within the range [βu, βc); μi-τin-ε is the membership degree of the accuracy of the τth evidence collection within the range [βu, βc), μ2-τin-ε is the membership degree of the integrity of the τth evidence collection within the range [βu, βc), μ2-τin-ε is the membership degree of the timeliness of the τth evidence collection within the range [βu, βc);
S13-1-d-3 when z3-τ is the maximum, the edge node Ai is trustworthy, the edge proxy computes means of membership degrees within a range [βc, 1] corresponding to accuracy, integrity and timeliness, which are
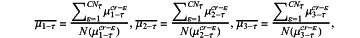 where a denominator represents the number of membership degrees of all factors within the range [βc, 1] and a numerator represents the sum of membership degrees of all factors within the range [βc, 1]; μ1-τcr-ε is the membership degree of the accuracy of the τth evidence collection within the range [βc, 1], μ2-τcr-ε is the membership degree of the integrity of the τth evidence collection within the range [c, 1], μ2-τcr-ε is the membership degree of the timeliness of the τth evidence collection within the range [βc, 1];
(S13-1-e) the edge proxy computes a direct trust value TrustAi-τcd the edge node Ai according to the average membership degree of accuracy, integrity and timeliness, and the weight thereof, the computing formula being as follows:
TrustAi-τcd=α1-τcd=α1-τ′μ1-τ+α2-τ′μ2-T+α3-τ′μ3-τ (4)
since the edge nodes to be operated have no historical trust values and feedback scores, at this moment, the initial direct trust value is the final trust value, and the final trust value before the edge node Ai operates is TrustAi-0u=TrustAi-0cd;
(S13-2) Computing Trust Identifier: edge node trust is divided into three levels, namely an untrustworthy level, an uncertain level and a trustworthy level;
a threshold of the untrustworthy level is βu, a threshold of the trustworthy level is βc, 0<βu<βc≤1 and βc=[1+10(ERAi)2]−1, βu=βc−0.2, where ERAi represents an error rate of computing errors allowed to be caused by each edge node Ai in an industrial production environment occasionally due to mistake, 0≤ERAi<30%, the greater the βu and βc, the sensitive the system to incorrect computing results; the security administrator sets an error rate of errors allowed to be caused by each edge node in an industrial production environment, and the edge proxy computes corresponding βu and βc according to the error rate;
the edge proxy computes a trust identifier of an edge node Ai to be operated according to a judgment result, the rules are as follows:
(S13-2-a) for an edge node of which the trust value level is a trustworthy level, in order to prevent a malicious node from cheating trust, the edge proxy replaces a trust value of the edge node with a trustworthy level with
 that is, degrades the edge node with a trustworthy level to an edge node with an uncertain level;
(S13-2-b) for an edge node of which the trust value level is an uncertain level, the edge proxy allocates a trust identifier TIAi-0=1 of an initial trust value to the edge node, computes valid time TAi-0v the initial trust identifier according to formula (5), and stores initial trust associated information locally;
a computing formula of the valid time TAi-0v the trust identifier of the initial trust value is as follows:
TAi-0v=5i×CN0×TAι-0×l+5ΔT (5)
where i represents a number of on-line edge nodes, CN0 represents a number of times of evidence collection in initial trust evaluation, TAι-0 represents an average computing efficiency
 of edge nodes Ai, l represents a data amount of evidence collection each time, ΔT represents a time interval between trust updates, and the valid time is in second; if a trust identifier of an edge node is expired, the edge proxy lists the edge node in a blacklist;
(S13-2-c) for an edge node of which the trust level is an untrustworthy level, that is, an edge node of which the z1-τ is the maximum, to avoid evaluation errors, the edge proxy repeats the above-mentioned steps of evidence collection, evidence processing and trust evaluation to evaluate the initial trust value thereof twice, if the trust value is still untrustworthy after being evaluated twice, reports to the security administrator to replace the edge node, and computes an initial trust value of the replaced edge node to be added;
initial trust associated data of the edge node Ai includes initial trust value evaluation start time t0, a node identity identifier IDAi, an accuracy membership degree mean μ1-0, an integrity membership degree mean μ2-0, a timeliness membership degree mean μ2-0, an initial trust value TrustAi-0u, a trust identifier TIAi-0 and valid time TAi-0v;
the edge proxy transmits the trust identifier to a site device, the site device checks the trust identifier of the edge node to be operated and then transmits data to an edge node with a trust identifier greater than 0, and then the edge node is in an operating state;
S2 After Network Operation:
S21 Evidence Collection: after a network operates for ΔT time, the edge proxy initiates an update trust request to the site device, the edge proxy starts to collect the collected data of the site device, a computing result of the edge node and a Hash value thereof, and a feedback score from the site device, records response time and a historical direct trust value of the edge node; after the edge proxy initiates the trust update request, the edge proxy conducts each evidence collection in following two cases:
case 1: the edge node directly returns the computing result to the site device, and the site device transmits the computing result of the edge node and the Hash value thereof to the edge proxy;
case 2: after preliminary computing, the edge node transmits the computing result and the Hash value thereof to the edge proxy, the edge proxy collects evidence and uploads the computing result of the edge node, trust identifier and signature to an industrial cloud, the industrial cloud checks the trust identifier of the edge node and verifies the signature and then further processes a preliminary computing result of the edge node, the industrial cloud transmits the computing result and the signature to the edge proxy, the edge proxy verifies the signature and then transmits the computing result to the site device;
the edge proxy collects evidence data in the above two cases, and collects l evidence data as one evidence collection; each round of trust update requires evidence collection for CNτ times, and the edge node is in an operating state at this moment; the edge proxy records the number of times of evidence collection with ε (ε=1, 2, . . . , CNτ); during the τth round of trust update, the edge proxy collects evidence for CNτ times and then conducts evidence processing and trust update operations; a time interval between every two rounds of trust updates is ΔT; a computing formula of the number of times of evidence collection CNτ required for the τth round of trust update is specified as follows:
CNτ=[6×arctan[0.5×TIAi-(τ-1)]] (6)
the edge proxy computes the number of times of evidence collection CNτ required for the τth round of trust update according to the trust identifier of the (τ−1)th time; the edge proxy rapidly updates the trust value of the edge node when the trust identifier is small and the number of times of evidence collection is less; at the initial stage of network operation, the number of times of evidence collection increases with the increase of the number of trustworthy times, in order to update the trust value in time and reduce trust computing amount, the number of times of evidence collection cannot be infinitely increased, and the maximum value of the number of times of evidence collection
 (S21-1) Direct Trust Factor Collection:
the site device transmits the collected data α0-τε to the edge proxy and the edge node Ai simultaneity, the site device transmits a piece of data every Δt, and the edge proxy and the edge node start processing after receiving the second collected data; the edge proxy processes a computing result of the data collected in two consecutive times as bϑ-τε, the edge node Ai processes a computing result of the data collected in two consecutive times as cϑ-τε, ϑ represents a serial number of evidence collected in each evidence collection, (ϑ=1, 2, . . . , l); during each evidence collection, the site device needs to transmit (l+1) data, and the data transmitted by the site device form a set
DataD-τc-ϑ={a0-τε,a1-τε,a2-τε, . . . ,a1-τε};
at tT, the edge proxy starts the τth round of trust update, the edge proxy collects evidence for CNτ times in total, l data evidence collected for the εth time including a computing result DataB-τr-ε={b1-τε, b2-τε, . . . , bϑ-τε, . . . , b1-τε} of the edge proxy, a computing result DataAi-τr-ε={c1-τε, c2-τε, . . . , cϑ-τε, . . . , c1-τε} of the edge node Ai and a Hash value DataAi-τh-ε={h1-τε, h2-τε, . . . , hϑ-τε, . . . , h1-τε} thereof, and a corresponding Hash value DataAi-τh′-ε={h1-τε′, h2-τε′, . . . , hϑ-τε′, . . . , h1-τε′} computed by the edge proxy according to the computing result set DataAi-τr-ε of the edge node Ai; the edge proxy records time tD-τs-ε of transmitting the first data by the site device when collecting evidence for the εth time, time tB-τr-ε computing the lth result by the edge proxy, and time tAi-τr-ε computing the lth result by the edge node Ai;
(S21-2) Historical Direct Trust Value Collection:
because trust dynamically changes with time, in order to avoid malicious acts, the edge proxy uses a historical direct trust value to correct a direct trust value, and the edge proxy uses a sliding window to store the historical direct trust value so as to reduce the influence of the old direct trust value on the new direct trust value; each edge node has a sliding storage window, the larger the window, the more the storage and computing overhead, so a short and small sliding storage window can limit the amount of trust computing and improve the efficiency of trust evaluation;
the sliding storage window includes u panes, each pane retains a historical direct trust value, that is, a direct trust value before the τth round of trust update is stored in the sliding storage window; a direct trust value stored in the k pane is TrustAi-(τ-u+k-1)cd; only when each pane has a direct trust value, the window begins to move, and moves one pane every time; a new direct trust value is added into the window after the trust is updated, while an expired direct trust value is extruded out of the window; during the τth round of trust update, direct trust values from the (τ−u)th round of trust update to the (τ−1)th round of trust update are stored in the window, and a direct trust value of the τth round is stored in the sliding storage window after the τth round of trust update; when a trust identifier of the edge node Ai is equal to 0, the edge node is regarded as a malicious node, and the edge proxy deletes a sliding storage window thereof,
(S21-3) Feedback Score Collection:
the edge proxy updates a final trust value of an edge node in an operating state and also needs to take into account a feedback score given to a computing result of the edge node by the site device; a rule of giving scores to edge nodes by the site device is as follows: if a safety accident occurs, the site device feeds back dϑ-τε=−1 regardless whether a trust update is being conducted, and the edge proxy lists an edge node corresponding to the feedback score in a blacklist; otherwise, the site device feeds back scores given to computing results: bad review dϑ-τε=0 and good review dϑ-τε=1;
the site device feeds back the scores given to the computing results to the edge proxy, during the τth round of trust update, the edge proxy collects for CNτ times and collects l feedback scores each time, and a feedback score collected by the edge proxy for the εth time is DataAi-τf-ε={d1-τε, d2-τε, . . . , dϑ-τε, . . . , dl-τε} including scores given, by the site device, to computing results directly returned by v edge nodes to the site device and scores given, by the site device, to computing results transmitted by (l−v) edge nodes to the industrial cloud for processing and then returned to the site device; a proxy signature based on elliptic curve is used to make the communication between the edge nodes and the industrial cloud trustworthy, no matter the computing results received by the site device come from the edge nodes or the industrial cloud, the objects to which the site device feeds back scores are edge nodes;
S22 Evidence Processing:
(S22-1) Direct Trust Factor Processing:
after collecting evidence for CNτ times, the edge proxy respectively computes accuracy, integrity and timeliness of an edge node Ai during each evidence collection in the τth round of trust update;
(S22-1-a) the edge proxy computes accuracy of the edge node Ai according to formula (1);
(S22-1-b) the edge proxy computes integrity of the edge node Ai according to formula (2);
(S22-1-c) according to the time tD-τs-ε of transmitting the first data by the site device when collecting evidence for the εth time, the time tB-τr-ε of computing the lth result by the edge proxy, and the time tAi-τr-ε computing the lth result by the edge node Ai, the edge proxy computes a computing efficiency
 of the edge node and a computing efficiency
 of the edge proxy, substitutes TAi-τtm-ε, TB-τtm-ε into formula (3), and compute timeliness of the edge node Ai;
when conducting the τth round of trust update, the edge proxy processes the collected direct trust factors by means of formula (1), formula (2) and formula (3), to obtain CNτ values of each of accuracy, integrity and timeliness of an edge node Ai to be examined;
(S22-2) Historical Trust Value Processing:
for weight factors of historical direct trust values at different time, there is a need to take into account a time factor, that is, the longer the time of the trust value, the lower the proportion; a weight of the kth pane of the sliding storage window is:
φk=e−ρ(u-k) (7)
where ρ represents an attenuation coefficient which is 0.3; if the sliding storage window is not fully stored, u is the number of actual historical direct trust values;
according to the historical direct trust value and weight thereof in the sliding storage window, the edge proxy computes a weighted average historical trust value TrustAi-τhd of the edge node Ai in the τth round of trust update:
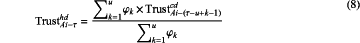 (S22-3) Feedback Score Processing:
for an edge node with a feedback score of −1, the security administrator replaces the edge node with an edge node to be added, and the edge proxy repeats an initial trust value computing step, to evaluate an initial trust value of the edge node to be added;
according to the feedback score, the edge proxy computes reward and penalty factors of the edge node Ai in the τth round of trust update; and according to a difference ΔNAi-tε=NAi-τg-ε−└l×(1−ERAi)┘ between the total number of times of good review NAi-τg-ε during evidence collection for the εth time and the minimum required number of correct computing results, the edge proxy computes a reward factor EAi-τg-ε and a penalty factor EAi-τb-ε corresponding to the evidence collection for the εth time, where NAi-τg-ε=Σϑ=1ldϑ-τε, ERAi is the error rate that the edge node is allowed to calculate in an industrial production environment;
if ΔNAi-τε≥0, the reward factor and penalty factor corresponding to the evidence collection for the εth time are EAi-τg-ε=0.3[(1+e−ΔNAi-τε)−1−0.5] and EAi-τb-ε=0 respectively; otherwise, the reward factor and penalty factor corresponding to the evidence collection for the εth time are EAi-τg-ε=0 and EAi-τb-ε=0.4[(1+e−ΔNAi-τε)−1−0.5] respectively; the reward degree is small and the penalty degree is large, which reflects the characteristic that the trust value is slowly increased and quickly decreased;
the edge proxy computes a final reward or penalty factor EAi-τf according to the reward and penalty factors in the τth round of trust update:
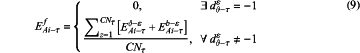 good feedback from the field device increases the trust value of the edge node Ai and bad feedback rapidly decreases the trust value of the edge node Ai; if there is safety accident feedback from the site device, EAi-τf appears as a penalty factor, EAi-τf=0; if there is no safety accident feedback, EAi-τf>0 represents reward, EAi-τf<0 represents penalty, and EAi-τf=0 represents neither reward nor penalty;
S23 Trust Update:
according to the direct trust value, historical trust value and feedback scores, the edge proxy updates the trust value of the edge node, the edge node is in a to-be-examined state at this moment; a time interval between every two rounds of trust updates is ΔT;
(S23-1) Computing Direct Trust Value:
the edge proxy repeats the step of computing a direct trust value when evaluating initial trust, and computes a direct trust value TrustAi-τcd of the edge node Ai to be examined of which the judgment result is trustworthy or uncertain in the τth round of trust update by means of formula (4); for an edge node to be examined of which the judgment result is untrustworthy, the edge proxy directly lists the edge node in a blacklist;
(S23-2) Correcting Direct Trust Value:
before computing the final trust value, the edge proxy needs to correct the direct trust value by using the weighted average historical direct trust value; the edge proxy weights and aggregates TrustAi-τcd and TrustAi-τhd of the edge node Ai to obtain a corrected direct trust value TrustAi-τd the edge node Ai in the τth round of trust update:
TrustAi-τd=δ×TrustAi-τcd+(1−δ)×TrustAi-τhd (10)
where δ is used to balance proportions of current trust and historical trust, and δ is defined as follows:
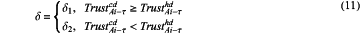 where 0<δ1<δ2<1, it is specified that δ1=0.3, δ2=0.7, the value of δ1 is small, to prevent the edge node from accumulating trust thereof quickly, and the value of δ2 is large, which reflects a penalty for a malicious act of the edge node;
(S23-3) Updating Final Trust Value:
according to the reward or penalty factor computed in formula (9), the edge proxy computes a final trust value of the edge node to be examined;
a computing formula of the final trust value TrustAi-τu of the edge node Ai in the τth round of trust update is as follows:
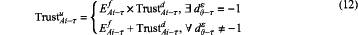 if a certain feedback score is −1, the final trust value of the edge node Ai in the τth round of trust update is equal to 0; otherwise, the final trust value of the edge node Ai in the τth round of trust update is equal to a corrected direct trust value of the edge node Ai plus a reward or penalty factor;
(S23-4) Computing Trust Identifier:
after trust update, the edge proxy compares the final trust value of the edge node to be examined with a trust value in Table 2-trust level table, and then computes a trust identifier of the edge node Ai according to the judgment result and the final trust value, rules are as follows:
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
(S23-4-a) for an edge node of which the trust value level is a trustworthy level, the edge proxy computes a trust identifier TIAi-τ thereof according to formula (13), computes valid time TAi-τv the trust identifier according to formula (14), and then stores trust associated information thereof locally according to a data structure in Table 6;
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
a specific computing formula of the trust identifier of the edge node Ai in the τth round of trust update is as follows:
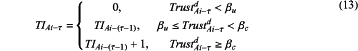 a computing formula of the valid time TAi-τv of the trust identifier of the trust value is as follows:
TAi-τv=6×CNτ×l×(TAι-τ+Δt)+TIAi-τ×ΔT (14)
where CNτ represents a number of times of evidence collection required in the τth round of trust update, l represents a data amount of evidence collection each time, TAι-τ represents an average computing efficiency
 of edge nodes Ai, Δt represents a time interval at which the site device transmits data, ΔT represents a time interval between trust updates, and the valid time is in second; if a trust identifier of an edge node is expired, the edge proxy lists the edge node in a blacklist;
(S23-4-b) for an edge node of which the trust level is an uncertain level, a trust identifier thereof is unchanged; the edge proxy checks the trust identifier thereof, and if the number of times of continuous equality of the trust identifier is less than 3, the edge proxy allows the edge node to operate; otherwise, the edge proxy lists the edge node in a blacklist, and then the edge node is in an isolation state;
(S23-4-c) for an edge node of which the trust level is an untrustworthy level, the edge proxy lists the edge node in a blacklist directly, and then the edge node is in an isolation state; the edge proxy broadcasts identity information about the edge node in the blacklist and a trust identifier 0 thereof, and reports to the security administrator to replace the edge node; after the security administrator replaces the isolated edge node with an edge node to be added, the edge proxy repeats an initial trust value computing step, to separately evaluate an initial trust value of the edge node to be added;
trust associated data of the edge node Ai includes start time tτ of the τth round of trust update, a node identity identifier IDAi, an average accuracy membership degree μ1-τ, an integrity membership degree mean μ2-τ, a timeliness membership degree mean μ3-τ, a corrected direct trust value TrustAi-τd, a reward or penalty factor EAi-τf, a final trust value TrustAi-τu, a trust identifier TIAi-τ and valid time TAi-τv;
the edge proxy transmits the trust identifier to the site device, the site device decides whether to transmit data according to the trust identifier of the edge node, and transmits data to an edge node with a trust identifier greater than 0 rather than to an edge node with a trust identifier equal to 0;
after ΔT time, the edge proxy repeatedly executes the steps of evidence collection, evidence processing and trust update.
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||