| CPC H04L 9/3247 (2013.01) [H04L 9/0643 (2013.01); H04L 9/0825 (2013.01); H04L 9/3073 (2013.01); H04L 9/3213 (2013.01); H04L 63/168 (2013.01)] | 18 Claims |
|
1. A computer-implemented method, comprising:
under control of one or more processors:
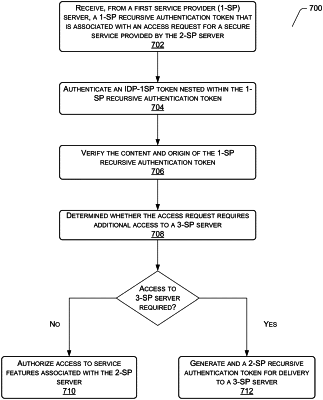
receiving, at a second service provider (2-SP) server, a service request to access a secure service provided by a first service provider (1-SP) server;
determining that an additional secure service is required from a third-party service provider (3-SP) server to fulfill the service request;
calculating a cryptographic hash of a 2-SP payload indicating the additional secure service;
generating a 2-SP public-private key pair that is associated with the 2-SP server;
generating a 2-SP digital signature based at least in part on the cryptographic hash and a private key of the 2-SP public-private key pair;
generating a 2-SP recursive authentication token (i) that is associated with the 2-SP server for delivery to the 3-SP server and (ii) that includes the 2-SP digital signature and the 2-SP payload; and
transmitting the 2-SP recursive authentication token to the 3-SP server.
|