| CPC H04L 63/1416 (2013.01) [G06F 18/23 (2023.01); H04L 63/1425 (2013.01); H04L 63/145 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
|
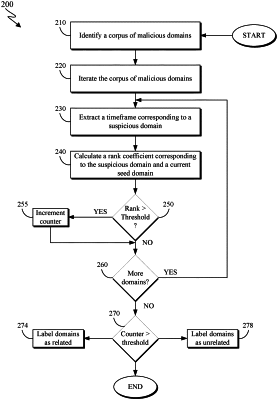
1. A computer implemented method for classifying domains to malware families, the method comprising:
identifying a corpus of malicious domains;
identifying one or more suspicious domains;
extracting a timeframe corresponding to the one or more suspicious domains;
calculating a rank correlation coefficient between the one or more suspicious domains and a current seed domain of the corpus of malicious domains;
determining whether the rank correlation coefficient exceeds a rank threshold for the one or more suspicious domains to provide a similarity count indicating a number of suspicious domains of the one or more suspicious domains whose rank correlation coefficients exceed the rank threshold;
comparing the similarity count to a relation threshold; and
responsive to determining the similarity count exceeds the relation threshold, applying a tag to the one or more suspicious domains indicating that the one or more suspicious domains correspond to a same malware family as the current seed domain.
|