| CPC H04L 63/0471 (2013.01) [G06F 3/062 (2013.01); G06F 3/0655 (2013.01); G06F 3/067 (2013.01); G06F 21/602 (2013.01); G06F 21/62 (2013.01); G06F 21/645 (2013.01); G06Q 20/38215 (2013.01); G06Q 20/3829 (2013.01); G06Q 20/383 (2013.01); G06Q 20/401 (2013.01); H04L 9/0643 (2013.01); H04L 9/0819 (2013.01); H04L 9/0825 (2013.01); H04L 9/083 (2013.01); H04L 9/0833 (2013.01); H04L 9/0891 (2013.01); H04L 9/14 (2013.01); H04L 9/30 (2013.01); H04L 9/3218 (2013.01); H04L 9/3236 (2013.01); H04L 9/3242 (2013.01); H04L 9/3247 (2013.01); H04L 9/3263 (2013.01); H04L 9/3265 (2013.01); H04L 9/3268 (2013.01); H04L 63/0421 (2013.01); H04L 63/0442 (2013.01); H04L 63/083 (2013.01); H04L 63/101 (2013.01); H04L 63/102 (2013.01)] | 13 Claims |
|
1. A method, comprising:
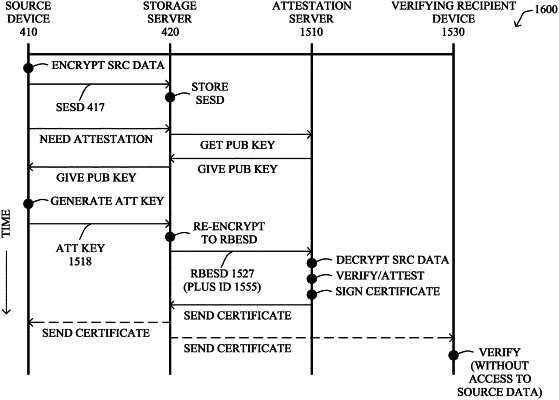
participating, by an attestation server, in a data storage system, wherein a storage server is configured to i) obtain source data from a source, wherein no device other than the source is able to read the source data; ii) obtain respective conversion keys specific to respective recipients from the source; iii) convert, in response to a request to share the source data with a particular recipient, the source data into a format readable only by the particular recipient based on a particular conversion key specific to that particular recipient;
receiving, at the attestation server from the storage server, the source data converted into a format readable by only the attestation server based on an attestation server conversion key specific to the attestation server;
attesting, by the attestation server, to the source data;
creating, by the attestation server, a signed certificate based on attesting to the source data, the signed certificate to allow a verifying recipient to confirm that the source data has been attested to by the attestation server based on the signed certificate, wherein the signed certificate is associated with the source data; and
sharing, from the attestation server, the signed certificate to cause the verifying recipient, without having access to the source data, to confirm that the source data has been attested to by the attestation server based on the signed certificate.
|