| CPC H04L 63/0414 (2013.01) [H04L 63/102 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); H04L 67/02 (2013.01); H04L 67/14 (2013.01)] | 6 Claims |
|
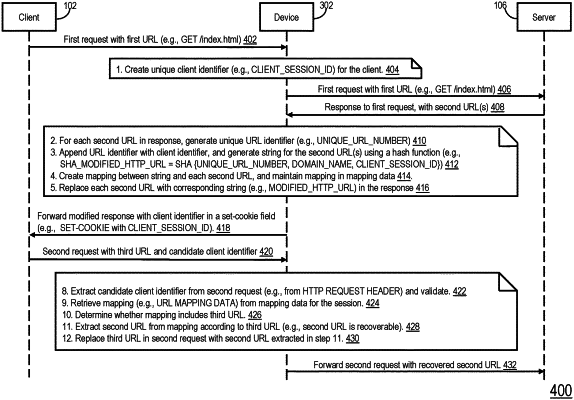
1. A method comprising:
receiving, by a device intermediary between a client device and a server in a session, a first request from the client device that includes a first uniform resource locator (URL) of the server;
receiving, by the device, a response from the server that includes a second URL;
updating, by the device, the response by including a client identifier uniquely identifying the client device for the session in a set-cookie field, obfuscating the second URL into a string, and replacing the second URL in the response with the string;
receiving, by the device, a second request that includes a candidate client identifier, and a third URL; and
determining, by the device, whether the second request is valid by:
matching the candidate client identifier with the client identifier;
determining whether mapping for the session includes the third URL;
determining whether the second URL is recoverable using the third URL;
identifying the second URL from the mapping according to the third URL; and
replacing, by the device, the third URL in the second request with the second URL;
wherein obfuscating the second URL into a string comprises:
generating, by the device, a URL identifier unique to the second URL; and
generating, by the device, the string by applying a hash function on a combination of the URL identifier, the client identifier and a domain name of the server.
|