| CPC G06Q 40/12 (2013.12) [G06Q 30/04 (2013.01); H04L 63/102 (2013.01); H04L 63/104 (2013.01)] | 19 Claims |
|
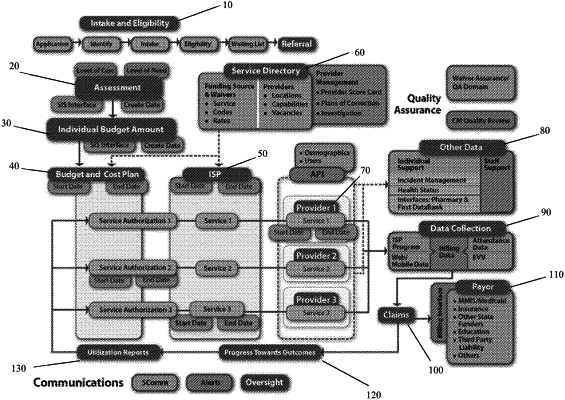
1. A HIPAA-compliant computer security method of real-time sharing of service, budget, and billing information associated with personal health information of one or more individuals among at least a first organization and a second organization in an integrated manner, and preventing unauthorized access to the billing information, the method comprising:
a. receiving by one or more physical nodes a first request for authorization for a user in the first organization to access service and budget information in the second organization pertaining to personal health information of one or more individuals, wherein the first organization is associated with a first security domain, the second organization is associated with a second security domain, the second organization has an access profile associated with the first security domain, the user is associated with one or more roles and one or more caseloads, the service and budget information for each of the one or more individuals having at least one type, the one or more roles includes access privilege information for one or more users, and the one or more caseloads includes access privilege information for at least one individual or medical services program associated with said individual's personal health information;
b. logging by the one or more physical nodes, in an activity log associated with at least the first organization or the second organization, the user's first request for authorization for the user in the first organization to access service and budget information in the second organization pertaining to the one or more individuals;
c. determining by the one or more physical nodes whether the user in the first organization is authorized to access service and budget information in the second organization pertaining to the one or more individuals, wherein the determination is based on at least the access profile, the one or more caseloads and the one or more roles associated with the user and the type of service and budget information in the second organization pertaining to the one or more individuals and associated with said individual's personal health information;
d. responsive to determining that the user in the first organization is authorized to access service and budget information in the second organization pertaining to the one or more individuals:
i. transferring by the one or more physical nodes the service and budget information in the second organization pertaining to the one or more individuals in compliance with HIPAA, and;
ii. logging by the one or more physical nodes, in the activity log, the transferring of service and budget information in the second organization pertaining to the one or more individuals to the user in the first organization in compliance with HIPAA; and
responsive to determining that the user in the first organization is not authorized to access service and budget information in the second organization pertaining to the one or more individuals, preventing the requested access in compliance with HIPAA; and
e. receiving, by one or more physical nodes, information pertaining to services provided to the one or more individuals by the first organization and billing information generated by the first organization pertaining to the provided services, wherein said information pertaining to services permits the user to monitor said services and the individual's progress toward outcomes.
|