| CPC G06F 9/45558 (2013.01) [G06F 21/577 (2013.01); H04L 63/00 (2013.01); G06F 2009/4557 (2013.01); G06F 2009/45587 (2013.01); G06F 2009/45595 (2013.01)] | 15 Claims |
|
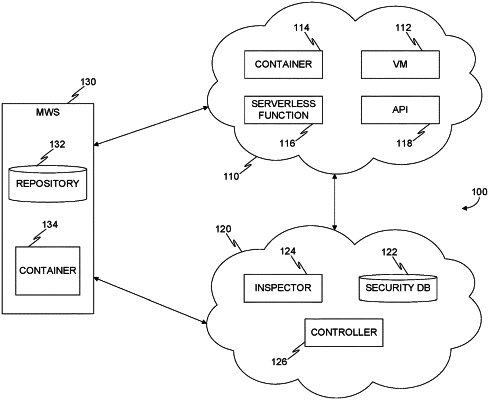
1. A method for inspecting running containers in a cloud computing environment for cybersecurity threats, comprising:
discovering a container running in a cloud computing environment;
detecting an identifier of the running container, wherein the identifier includes an indicator to a repository in which an image of the container is stored, the repository further storing a plurality of images, wherein a second image of the plurality of images does not correspond to a container running in the cloud computing environment;
accessing the repository to pull the image;
inspecting the image of the running container for a cybersecurity threat;
inspecting the image of the running container for the cybersecurity threat when the container is running in the cloud computing environment; and
configuring an inspector to halt inspection of an image not corresponding to a container running in the cloud computing environment.
|