| CPC G06F 3/065 (2013.01) [G06F 3/0619 (2013.01); G06F 3/0664 (2013.01); G06F 3/067 (2013.01); G06F 9/45533 (2013.01); G06F 21/602 (2013.01); G06F 2221/2107 (2013.01)] | 11 Claims |
|
1. A method for performing backup operations, the method comprising:
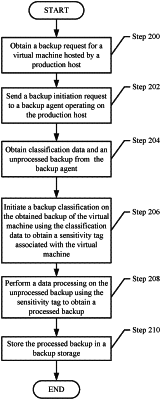
obtaining, by a backup server, a backup request, wherein the backup request specifies a virtual machine to be backed up, wherein the virtual machine is hosted by a production host, and wherein the virtual machine includes functionality for performing a process that provides a service to a user; and
in response to the backup request:
obtaining classification data from a backup agent, wherein the classification data specifies the functionality;
initiating a backup classification on an unprocessed backup associated with the virtual machine based on the classification data to obtain a sensitivity tag of sensitivity tags, wherein the sensitivity tags comprise a high sensitivity tag, a medium sensitivity tag, and a low sensitivity tag; and
initiating a data processing on the unprocessed backup based on the sensitivity tag,. wherein:
the sensitivity tag is determined to comprise the high sensitivity tag, and
in response to the determining, initiating the data processing, wherein the data processing comprises generating a processed backup by:
performing encryption on the unprocessed backup using a private key to generate an encrypted backup,
replicating the encrypted backup,
generating a digital signature of the encrypted backup,
extending a retention period associated with the encrypted backup, and
performing user authentication for access of the encrypted backup.
|